Mitigating CitrixBleed 2 (CVE‑2025‑5777) NetScaler Memory Disclosure with App & API Protector
On Friday, July 4, 2025, exploit details were publicly disclosed for a memory disclosure vulnerability affecting Citrix NetScaler ADC and Gateway devices. This is a pre-authentication flaw that allows attackers to craft malicious requests that leak uninitialized memory from affected NetScaler devices.
The vulnerability was originally made known to Citrix customers on June 17, 2025, and since then research organizations have shown activity surrounding the flaw, indicators of compromise, and an exploitation proof of concept. Even if you patched your affected devices quickly, it’s important to check for exposure now that the proof of concept has been made public. This flaw can have dire consequences, considering that the affected devices can be configured as VPNs, proxies, or AAA virtual servers. Session tokens and other sensitive data can be exposed — potentially enabling unauthorized access to internal applications, VPNs, data center networks, and internal networks.
Affected devices and versions:
- NetScaler ADC and NetScaler Gateway 14.1 BEFORE 14.1-43.56
- NetScaler ADC and NetScaler Gateway 13.1 BEFORE 13.1-58.32
- NetScaler ADC 13.1-FIPS and NDcPP BEFORE 13.1-37.235-FIPS and NDcPP
- NetScaler ADC 12.1-FIPS BEFORE 12.1-55.328-FIPS
Since the exploit disclosure, we have seen a drastic increase of vulnerability scanner traffic and additional threat actors searching for vulnerable targets. App & API Protector customers are protected with a special Rapid Rule 3000967 that was released to address this CVE.
Please note, there are a couple of other Citrix CVEs, as follows:
CVE‑2025‑6543: This is an unauthenticated memory overflow in Citrix NetScaler ADC/Gateway (VPN/AAA mode), which can disrupt control flow, cause denial of service, or even lead to remote code execution. But there is no public PoC available yet.
CVE‑2025‑5349: This is related to an improper access control flaw affecting the NetScaler Management Interface, which may lead to performing unauthorized administrative actions. There is no known public PoC at this time.
Vulnerability details
The underlying code of Citrix NetScaler is written in C or C++, and the vulnerability lies within the authentication function, which processes the login parameters.
The root cause is the use of an uninitialized login variable (intended to hold username details) combined with improper memory handling, lack of input validation, and missing error handling in Citrix NetScaler’s authentication logic. Since C and C++ do not automatically initialize variables to zero, null, or some other specified value, the uninitialized variables may point to random stack memory space and allow attackers to access unintended/sensitive data residing in this memory space — essentially leftover data from previous operations or processing.
The vulnerability targets the URL path /p/u/doAuthentication.do and requires no authentication, making it very accessible to attackers, and does not require any prior conditions. This combination of flaws enabled unauthenticated attackers to leak sensitive memory content, and certain threat actors have already begun exploiting it in the wild. The full impact and scope of affected victims and organizations still remains unclear.
Exploiting the vulnerability
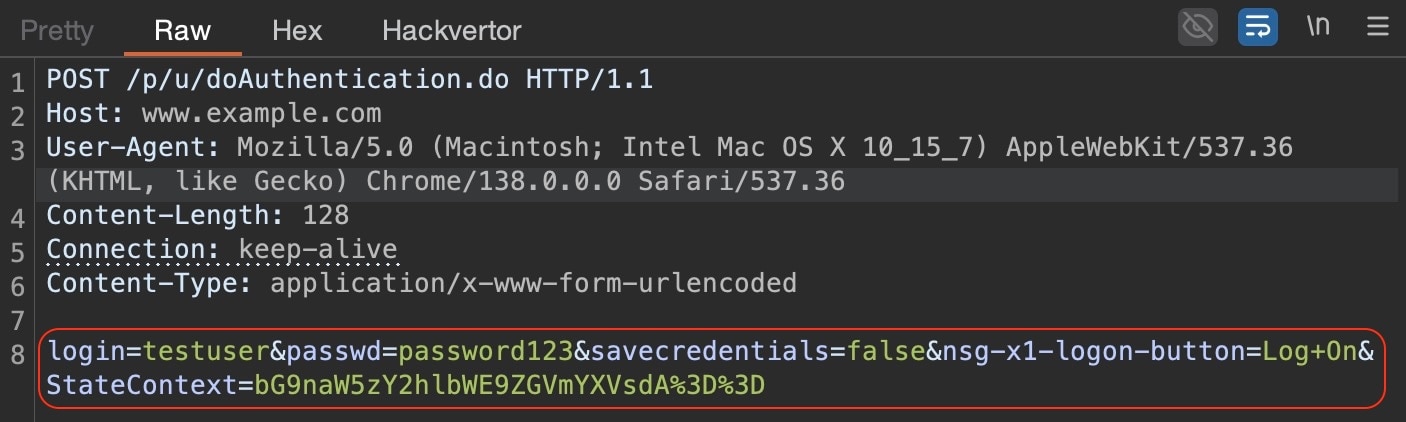
A legitimate POST request to perform authentication would include very expected parameter names like login, passwd, and additional parameters with corresponding values (Figure 1).
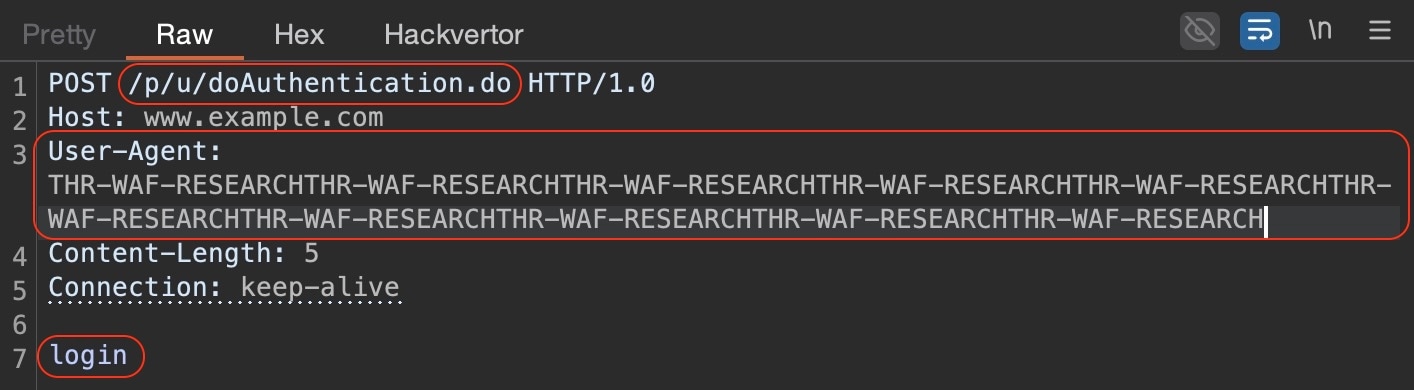
In an exploit attempt, there would also be a noticeably large attackers’ controlled payload in the User-Agent header and an HTTP body, which might only include the login string (Figure 2). This makes it more trivial to exploit.
Why is it called CitrixBleed?
The term “CitrixBleed” is used because the memory leak can be triggered repeatedly by sending the same payload, with each attempt leaking a new chunk of stack memory — effectively “bleeding” sensitive information. The long User-Agent header is used to inject a recognizable pattern into the stack. By flooding the memory with a large enough random string, such as THR-WAF-RESEARCH repeated many times, the attacker can ensure when the uninitialized stack bytes are leaked. Those distinctive markers will appear inside the <InitialValue>…</InitialValue> XML tags in the HTTP response body. This both confirms the leak as well as exposes chunks from the memory, which usually contains sensitive data, like session variables, tokens, passwords, usernames, or configuration values.
Just like the original CitrixBleed vulnerability (CVE‑2023‑4966) disclosed in 2023, which leaked memory via a malformed Host header, CitrixBleed 2 (CVE‑2025‑5777) also leaks memory this time due to the use of an uninitialized variable. The first issue was mitigated by the Akamai Ghost Servers by default, thanks to strict Host header validation, whereas CitrixBleed 2 requires a dedicated Adaptive Security Engine (ASE) rule.
Here is a simple recap of the exploitation steps:
1) Recon — Scan for exposed Citrix NetScaler ADC/Gateway instances.
2) Enumeration — Check if the target runs a vulnerable version.
3) Exploit — Send a crafted request to /p/u/doAuthentication.do with a long User-Agent header (no authentication needed).
4) Leak — The device responds with leaked stack memory in <initialValue> XML tags.
5) Bleeding phase — Steps 3–4 are repeated, causing continuous stack memory leaks (CitrixBleed 2) from the same target device.
6) Post-exploitation — Attackers use the leaked data for malicious purposes, like successfully authenticating with leaked session tokens.
App & API Protector mitigation
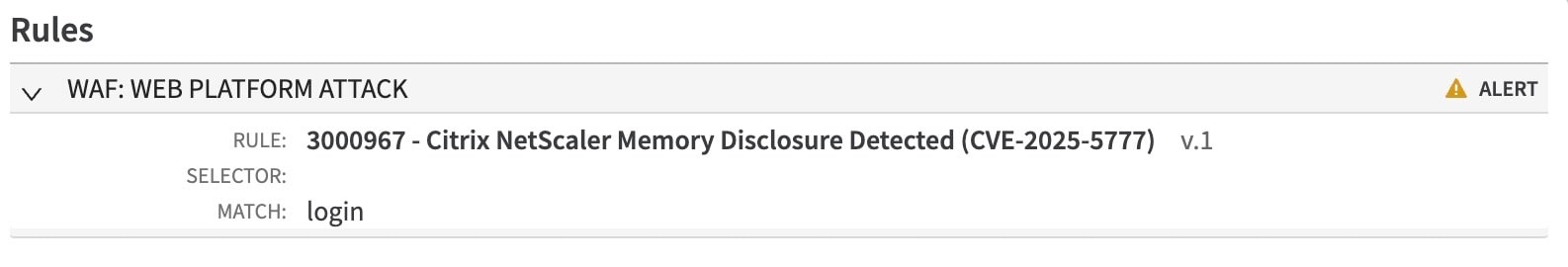
In response to CitrixBleed 2, the WAF Threat Research Team released a new Rapid Rule on July 7, 2025, with a default action set to “Alert”:
3000967 - Citrix NetScaler Memory Disclosure Detected (CVE-2025-5777)
After confirming the rule is accurate, the recommended Rapid Rule action was set to default action of “Deny” on July 8, 2025.
Exploitation details
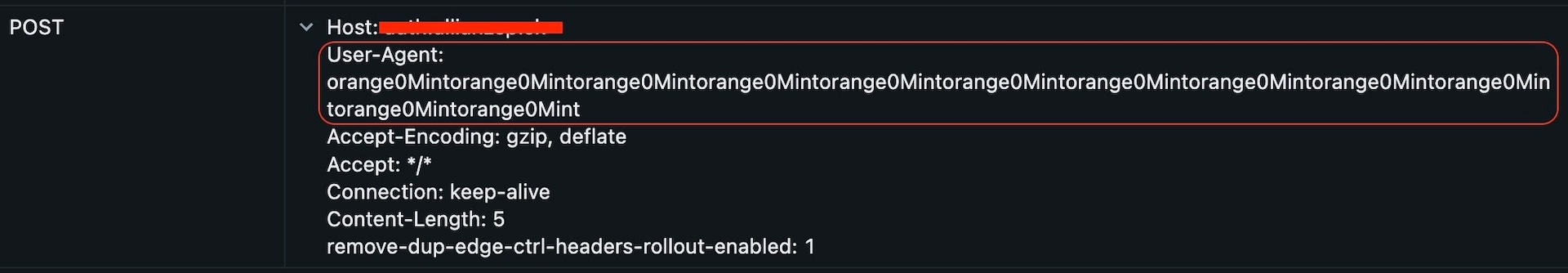
On July 8, we observed more than 200,000 POST requests targeting the URL path /p/u/doAuthentication.do across multiple hostnames and originating from various IP addresses. These do appear to be large-scale scanning attempts aimed at identifying vulnerable NetScaler instances. Figure 4 is a sample request we detected during this activity:
Final note
The Akamai SIG will continue to monitor, report on, and create mitigations for threats such as these for both our customers and the security community at large. To keep up with more breaking news from the Akamai Security Intelligence Group, check out our research home page and follow us on social media.