Akamai’s CDN includes origin servers, edge servers, and Domain Name System (DNS) servers. Origin servers are where the original versions of content are stored. Edge servers around the globe contain cached copies of the content stored on original servers. DNS servers direct requests for content to the most appropriate origin CDN server or caching server.
A content delivery network (CDN) is a group of geographically distributed servers that speed up the delivery of web content by bringing it closer to where users are.
CDNs rely on a process called “caching” that temporarily stores copies of files in data centers across the globe, allowing you to access internet content from a server near you. Content delivered from a server closest to you reduces page load times and results in a faster, high-performance web experience. By caching content like web pages, images, and video in servers near your physical location, CDNs allow you to do things like watch a movie, download software, check your bank balance, post on social media, or make purchases without having to wait for content to load.
You could think of a CDN like an ATM. If your money were only available from one bank in town, you’d have to make a time-consuming trip and stand in a long line every time you wanted to withdraw cash. However, with a cash machine on practically every corner, you have fast and easy access to your money any time you need it.
As content providers began delivering more rich web content such as graphics and video over the internet, CDN services were created to solve the problem of network congestion that resembled a traffic jam. Getting content from centrally located servers to individual users simply took too long. CDNs have now grown to include everything from text, graphics, scripts, and media files to software downloads, documents, portals, ecommerce, live streaming media, on-demand video streaming media, and social media sites.
For more than 20 years, CDNs have formed the unseen backbone of the internet — improving website performance and delivering online content for businesses quickly and at scale. Today, a large portion of all internet content is delivered through CDNs.
How does a CDN work?
A content delivery network relies on three types of servers.
- Origin servers. Origin servers contain the original versions of content and they function as the source of truth. Whenever content needs to be updated, changes are made on the origin server. An origin server may be owned and managed by a content provider or it may be hosted on the infrastructure of a third-party cloud provider like Amazon’s AWS S3 or Google Cloud Storage.
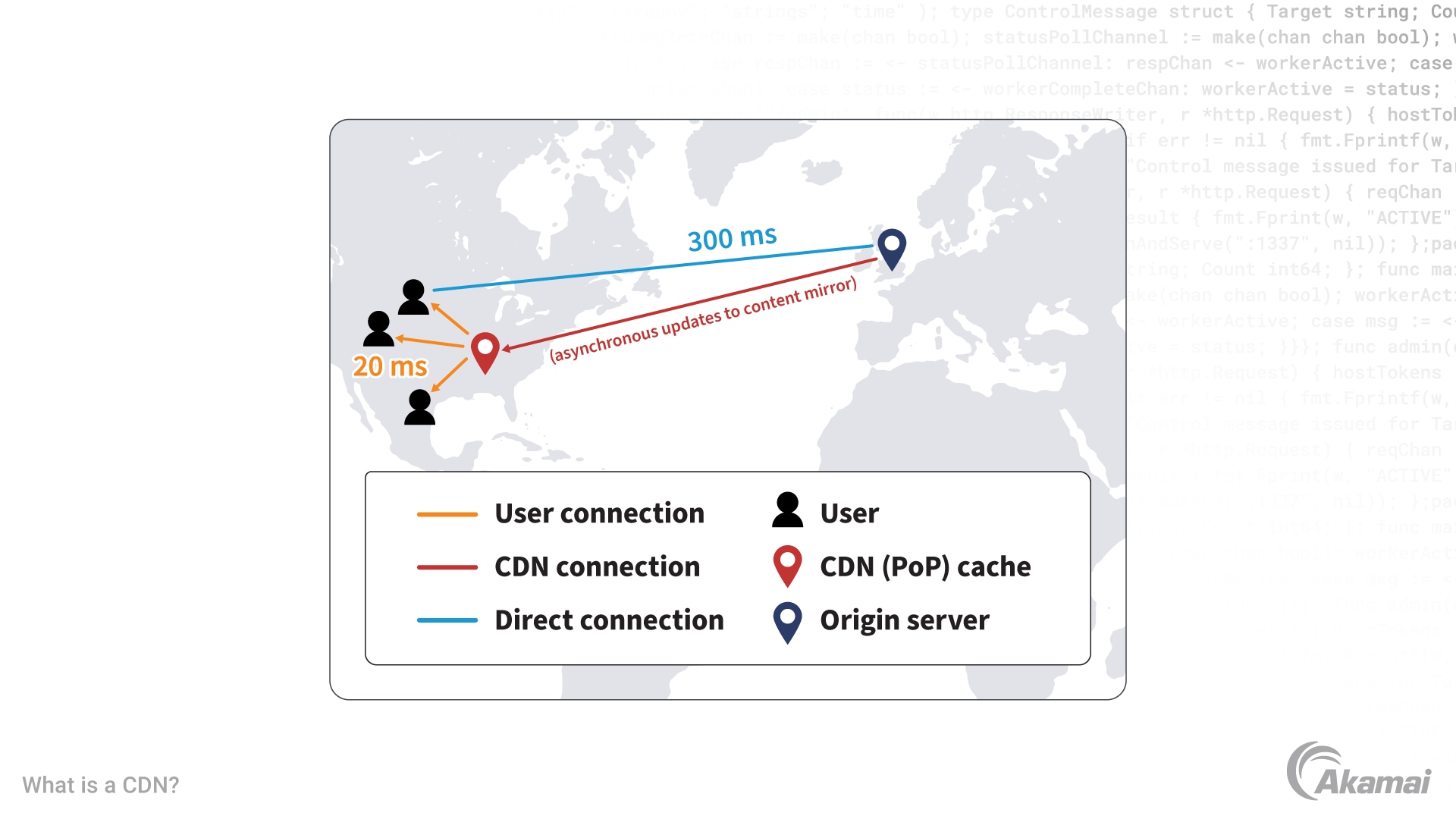
- Edge servers. Edge servers are located in multiple geographical locations around the world, also called “points of presence” (PoPs). The edge servers within these PoPs cache content that is copied from origin servers, and they are responsible for delivering that content to nearby users. When a user requests access to content on an origin server, they are redirected to a cached copy of the content on an edge server that’s geographically close to them. When cached content is out of date, the edge server requests updated content from the origin server. CDN edge servers are owned or managed by the CDN hosting provider.
- DNS servers. Domain Name System (DNS) servers keep track of and supply IP addresses for origin and edge servers. When a client sends a request to an origin server, DNS servers respond with the name of a paired edge server from which the content can be served faster.
A large portion of all internet content is delivered through CDNs. Here’s how it works in practice:
If you were in New York and wanted to view the website of your favorite store in London that’s hosted on a server in the U.K., you would experience slow content load times if the request had to travel all the way across the Atlantic Ocean. To remedy this, a CDN would store a cached version of the London website content in multiple geographical locations around the world (PoPs). These PoPs contain their own caching servers and are responsible for delivering that content close to where you’re located in New York.
To deliver the optimal viewing experience, CDNs perform two essential functions.
- Reduce latency. Latency is that annoying delay you experience when trying to access a web page or video stream before it fully loads on your device. Although measured in milliseconds, it can feel like forever, and it may even result in a load error or time-out. Some content delivery networks alleviate latency by reducing the physical distance that the content needs to travel to reach you. Therefore, larger and more widely distributed CDNs are able to deliver website content more quickly and reliably by putting the content as close to the end user as possible.
- Balance loads. A CDN balances overall traffic to give everyone accessing internet content the best web experience possible. Think about it like routing traffic in the real world. There may be one route that’s usually the fastest from point A to point B if no other cars take it — but if it starts getting congested, it’s better for everyone if the traffic gets spread out over a few different routes. That may mean that you get sent on a roadway that’s a few minutes longer (or milliseconds, when scaled to internet speeds), but you don’t get stuck in the traffic jam that’s forming on the shortest route. Load balancing enables content providers to handle increases in demand and large traffic spikes while still providing high-quality user experiences and avoiding downtime.
The benefits of a CDN
CDNs carry a large portion of the world’s internet traffic. They help solve the toughest challenges of delivering content over the internet. From small and medium content providers to the world’s large corporations, businesses everywhere take advantage of key CDN benefits to provide a seamless web experience to their customers.
- Boost performance. Performance is the difference between a click giving you immediate access to new content and a click followed by a seven-second wait while a page loads or a video buffers. That wait time is called “buffering” and is symbolized by a familiar swirling circle icon on the screen. To ensure high performance and minimize buffering, CDNs deliver content that’s been pre-saved on nearby servers on the CDN’s network rather than sending requests to origin servers which may be halfway around the world. If the content isn’t already pre-saved, the CDN uses its programmed knowledge of the necessary connections to overcome any challenges. Advanced CDNs use additional technologies that resolve any issues in the delivery of uncacheable dynamic content and to determine the appropriate type of content to deliver to different devices. With CDNs, content providers can deliver fast, quality web experiences to all their end users; no matter what location, browser, device, or network they’re connecting from. Web pages render more quickly, video buffering time is reduced, and website visitors stay more engaged.
- Ensure availability. Availability means that content remains accessible to end users even during periods of excessive user traffic when many people are accessing content at the same time or if there are server outages in some parts of the internet. When traffic loads peak at millions of requests per second, even the most powerful servers are put to the test. Without a content delivery network, all this traffic must be absorbed by a content provider’s infrastructure. This can cause failures and poor end-user experiences. The widely distributed server infrastructure offered by CDNs is designed to alleviate these issues. Advanced CDNs, with their highly distributed architecture and massive platform of servers, can absorb 100+ Tbps of traffic and make it possible for content providers to stay available to even larger user bases.
- Enhance security. CDNs can also improve website security with increased protection against malicious actors and threats like distributed denial-of-service (DDoS) attacks. Today’s most advanced content delivery networks provide unique cloud-based security solutions and DDoS protection.
- Gather intelligence. As carriers of nearly half of the world’s internet traffic, CDN providers generate vast amounts of data about end-user connectivity, device types, and browsing experiences across the globe. This data can provide CDN customers with critical, actionable intelligence and insights into their user base. Intelligence from CDNs also enables services such as real user monitoring, media analytics that measure end-user engagement with web content, and cloud security intelligence to keep track of online threats.
- Improve customer experiences. Content, application, and website owners — including ecommerce sites, media properties, and cloud computing companies — use CDNs to improve customer experiences, lower abandonment rates, increase ad impressions, improve conversion rates, and strengthen customer loyalty.
- Offload traffic. With the explosive growth of online streaming and other rich media services, and higher user expectations about web performance across multiple device types, many of today’s network service providers are finding their content distribution networks to be highly stressed. By responding to a request for web content with a cached version from servers closer to the end user, a CDN can offload traffic from content servers and improve the web experience.
- Reduce bandwidth costs. By delivering content from servers closer to users, CDNs reduce bandwidth consumption and the associated costs.
Who uses CDNs?
Almost everyone that accesses the web uses a CDN. They were created to provide a faster and more reliable experience for people accessing the internet. They are used by the content and application owners and network service providers that supply those benefits to their customers.
CDNs for end users
Websites and web applications delivered through a CDN experience faster page loads, faster transactions, and a more consistent online experience. However, people may have no idea they are connecting through a content delivery network as they enjoy its benefits, because the technology works behind the scenes. They simply receive what they requested from their ISP or mobile provider.
CDNs for content owners
Content and application owners use CDNs to improve customer experiences. Using a content delivery network can also improve web security, for instance by helping to absorb and mitigate a DDoS attack.
CDNs for network service providers
Many of today’s network service providers are finding it necessary to deploy their own content distribution networks. For network operators, deploying a content delivery network can reduce subscriber churn, facilitate the development of value-added services, reduce traffic on the core network, and enable operators to sell CDN services to enterprises and third-party content owners.
One of the biggest benefits of a CDN is offload. By responding to a request for web content with a cached version in closer physical and network proximity to the end user — instead of from the server where the content originates — a CDN offloads traffic from content servers and improves the web experience. This means that content can stay within the network operator’s network and reduce the need to engage in peering with other networks or navigating the broader internet to deliver information.
CDN solutions from Akamai, the latest in edge delivery
Akamai’s CDN services were born from a challenge posed by internet founder Tim Berners-Lee, to solve what came to be known as the “World Wide Wait.” We pioneered edge computing more than 25 years ago by developing sophisticated new techniques to route web traffic, getting content from centrally located servers to early internet users faster. Today, the world’s biggest brands trust Akamai’s solutions and expertise to protect and deliver their digital experiences.
Akamai has an unmatched edge capacity of 1+ Pbps and is unparalleled at scale with more than 4,100 locations and upward of 1,200 networks that span 120+ countries. With the largest edge delivery platform, we see more of what’s happening on the internet. This means we can deftly avoid bottlenecks and defend at the edge.
No matter the type of content — websites, apps, APIs, video, or software — our comprehensive set of content delivery solutions is designed to deliver amazing digital experiences for every user, regardless of location, device, or network.
- App and API performance. Akamai app and API performance solutions improve user experiences with fast, engaging app and API performance. Akamai API Acceleration optimizes API performance and availability to enhance user experiences. Akamai Ion delivers fast, engaging, and reliable user experiences on sites and apps. Global Traffic Management optimizes app performance and avoids outages with intelligent load balancing.
- Media delivery. Akamai media delivery solutions consistently deliver exceptional streaming media services to the largest audiences, on any device. Akamai Adaptive Media Delivery delivers consistent, high-quality online video securely at massive scale, while Akamai Download Delivery delivers large file downloads flawlessly every time. Akamai Media Services Live delivers a broadcast-quality experience to viewers of live video streaming. Akamai DataStream delivers an inside look at the performance of CDNs and streaming media servers with log data at scale.
- Edge compute. Akamai edge applications lower overhead by running capabilities integrated on CDNs. Serverless computing solutions boost performance and UX by enabling developers to build web applications closer to end users. And cloud optimization technology improves availability and performance while reducing cloud application costs and complexity.
With Akamai’s CDN services, content and application owners and network services providers can:
- Deliver the best website and mobile app experiences imaginable with automated acceleration. Today’s users demand visually engaging, personalized experiences that are fast on every device, all the time. To deliver on customer expectations, Akamai technology continuously analyzes, optimizes, and accelerates web and mobile app experiences.
- Deliver high-quality video playback experiences to any screen. Online audiences expect fantastic video playback at all times, despite the many challenges of delivering online content. Akamai solutions optimize content and technology to provide consistent, high-quality video playback experiences across any screen to growing online audiences.
- Enable seamless download delivery. End users expect frictionless download experiences, combining fast downloads and nearly instant updates. To maximize download completion rates, customer satisfaction, and revenue, Akamai provides reliable, high-performance solutions that deliver large, file-based content over the internet.
- Accelerate API performance. APIs play a critical role in today’s fast-paced digital environment where connection speeds are measured in milliseconds. To handle the rapidly increasing number of API requests while ensuring reliability, scalability, and performance, Akamai accelerates delivery of APIs and other small payload traffic to enable fast and engaging user experiences across apps and sites. Akamai offloads requests from origin infrastructures and provides predictable high performance for large volumes of XML, JSON, and other small transactional and programmatic traffic types critical to application success.
Frequently Asked Questions (FAQ)
A CDN is a group of geographically distributed servers that speed up the delivery of web content by bringing it closer to the location of the users accessing the content. Data centers across the globe use caching, a process that temporarily stores copies of files, so that users can access internet content from a web-enabled device or browser more quickly through a server near them.
While CDNs and cloud computing were developed to address performance and scalability created by the demand for web content and applications, these technologies have fundamentally different focuses. Cloud computing environments offer computing resources like servers, databases, application, networking, and analytics as services over the internet. The cloud helps businesses lower upfront costs, scale application infrastructure as needed, expand into new geographies without having to invest in costly new infrastructure, and take advantage of related cloud services to build the latest digital experiences or enterprise applications. In contrast, a CDN is a network of servers that distributes content from an “origin” server throughout the world by caching content close to where each end user is accessing the internet via a web-enabled device. By reducing the distance that data and content has to travel, CDNs help reduce latency, deliver better user experiences, and decrease stress on origin servers by distributing the load geographically across multiple servers.
A CDN host is a service provider that offers access to a content delivery network for content and application owners. For network operators that are struggling to keep up with the never-ending demand for online video, a CDN hosting platform can be a highly effective and cost-efficient alternative to a web hosting provider. A content delivery network can enable operators to provide a fast, secure, reliable online experience with the consistent quality that people expect on every web-enabled device.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.