A grey hat hacker operates in the space between white hat and black hat hackers. While white hats follow strict ethical standards and obtain permission before testing systems, grey hats may expose security flaws without authorization. However, unlike black hats, their intent isn’t always malicious. Grey hats often reveal vulnerabilities to organizations to help fix them, but their methods can blur ethical and legal lines.
Are you familiar with the terms white hat and black hat hacking? If not, then you should know that they describe different approaches to exposing cybersecurity vulnerabilities. White hats, also known as ethical hackers, use their skills to help organizations protect their data and systems, while black hats — also known as malicious hackers or unethical hackers — are more sinister in nature and attempt to gain unauthorized access to data or systems. But what about grey hats?
Grey hat hackers are a unique subset of computer experts who exist between white hat and black hat hacking. The term grey hat refers to an individual who operates without malicious intent but still violates laws or acceptable standards of behavior by exploiting security vulnerabilities without permission. These individuals usually have enough technical expertise that they can identify weaknesses in networks and software that others may have overlooked.
Unlike black hats, grey hats do not attempt to cover up their activities; instead, they will often alert organizations about security issues they have discovered and provide advice on how best to resolve them. This means that instead of causing damage with their actions, grey hats can actually improve cybersecurity measures by pointing out potential vulnerabilities before they are exploited by malicious actors. Bug bounty programs are a popular way that many grey hats earn rewards while helping organizations improve their security measures — these programs involve identifying bugs or flaws within an organization’s software before anyone else can exploit them.
However, some organizations view even this type of activity as a threat due to its potential for misuse or abuse. For instance, if a grey hat hacker discovers a vulnerability in an organization’s system but does not let them know about it, and instead opting to sell the information or exploit it for personal gain, then this would be considered unethical at best and illegal at worst.
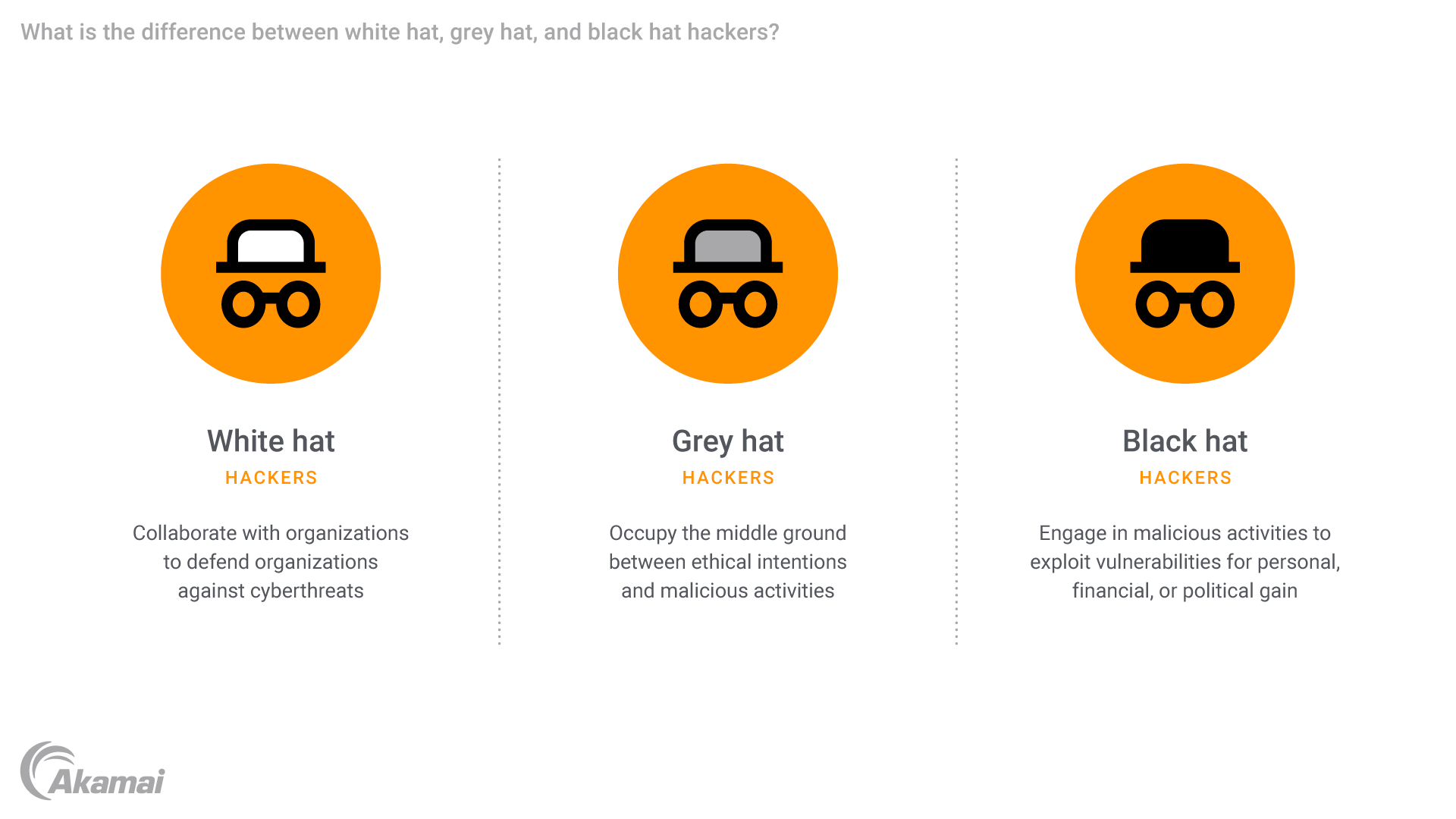
What is the difference between white hat, grey hat, and black hat hackers?
White hat hackers
White hat hackers are cybersecurity professionals who use their technical skills to defend organizations against cyberthreats. Operating within legal and ethical boundaries, white hats are often hired by companies to identify vulnerabilities, perform penetration testing, and develop robust security solutions. They work to safeguard computer systems, networks, and sensitive data from malicious actors, ensuring that security protocols are up to date and resilient against emerging threats.
White hats typically collaborate with organizations through formal channels such as bug bounty programs, security audits, or full-time employment in cybersecurity roles. Their objective is to uncover and address weaknesses in computer systems before they can be exploited by cybercriminals. This ethical approach helps companies maintain strong cyber defenses, prevent data breaches, and comply with information security regulations.
Grey hat hackers
Grey hat hackers occupy a middle ground between the ethical intentions of white hats and the malicious activities of black hat hackers. While grey hats often seek to identify vulnerabilities in computer networks and systems, they do so without permission, which can lead to legal and ethical concerns. Unlike black hats, grey hat hackers don’t typically exploit the vulnerabilities they find for personal gain; instead, they often report these flaws to the system owners or the broader cybersecurity community. However, since their actions involve unauthorized access, grey hat hacking may still be illegal depending on the jurisdiction.
Grey hats play a complicated role in cybersecurity. On the one hand, their discoveries can lead to better incident management and improved system defenses. On the other hand, their actions can expose security flaws that might not have been addressed otherwise, potentially leading to exploitation by more malicious actors if not reported or handled responsibly. Organizations need to weigh the benefits and risks when deciding whether to engage with grey hats, especially through mechanisms like responsible disclosure policies or bug bounty programs.
Black hat hackers
Black hat hackers are the antagonists of the cybersecurity world, engaging in illegal and malicious activities to exploit vulnerabilities in computer systems for personal, financial, or political gain. These hackers use their expertise to bypass security protocols, steal sensitive data, install malware, and conduct cyberattacks such as DDoS (distributed denial-ofservice), ransomware, and phishing campaigns. Black hats are motivated by various factors, including financial incentives, ideological reasons, or simply the desire to cause disruption.
Unlike white hats and grey hats, black hat hackers operate entirely outside the law, often targeting companies, governments, or individuals to exploit weaknesses for profit. Their activities pose significant risks to organizations, leading to data breaches, financial loss, and reputational damage. Cybercriminals of this type use a wide array of tools, including malware backdoor access, and bots to infiltrate computer networks and avoid detection, making them one of the most dangerous adversaries in the realm of cybersecurity.
What are the pros and cons of grey hat hacking?
In view of all of these factors, it’s important that organizations carefully consider all aspects prior to making an informed decision regarding engaging with grey hat hackers. While enlisting ethical ones can bring numerous benefits and help protect against malicious attacks, it is essential that companies take all possible risks into account before taking action.
The concept of grey hat hacking is a contentious one, and it’s imperative that organizations fully assess the advantages and drawbacks before deciding whether or not to engage with these hackers.
On the bright side, grey hats are able to offer businesses precious knowledge about their security systems. By reporting on the vulnerabilities they find, they can aid organizations in pinpointing weaknesses in their defenses before malicious attackers have a chance to exploit them. This enables companies to strengthen their protection without compromising their reputation or violating any laws. Furthermore, some hackers participate in bug bounty programs or offer penetration testing services for financial gain, potentially providing mutual benefits.
However, there are potential risks associated with allowing grey hats access to critical data and networks. Unscrupulous hackers may leverage this access for personal gain, like stealing data or extorting money. There’s also the possibility that ethical hackers could still misuse discovered weaknesses by deploying them without informing the responsible organization first.
Additionally, certain grey hat activities may be subject to legal penalties depending on the jurisdiction you live in: Getting apprehended by police while performing such activities without permission from the target company could lead to serious consequences.
Is grey hat hacking legal?
The legality of grey hat hacking is often a source of confusion, as it varies from place to place. In the United States, unauthorized access to computers or networks is illegal. However, if a system owner gives explicit permission for certain activities, these actions may be allowed. Other countries have different laws and regulations regarding this type of activity; some with strict penalties for unapproved entry and others with more lax rules.
For those considering engaging in grey hat hacking activities, it’s important to become familiar with local laws and ethical considerations before proceeding. Ignorance of the law cannot be used as a defense if an individual is caught breaking it. Additionally, data security and privacy should always be taken into account when dealing with confidential information or privileged systems.
Organizations can choose to work with grey hats legally by enacting responsible disclosure policies that allow hackers to report vulnerabilities in exchange for recognition or reward. But before entering into such an agreement, organizations must carefully evaluate all risks involved and consult legal counsel when deemed necessary. It’s up to each individual business to decide whether the potential benefits outweigh the associated risks when working with a grey hat hacker, based on their unique needs and goals. Being aware of the different types of hackers available helps companies create informed cybersecurity strategies that protect against malicious attacks while still taking advantage of expert knowledge in the field.
Grey hat hacking: Ethical implications and cybersecurity
Grey hat hackers occupy a unique and often controversial space in the world of cybersecurity. Unlike white hat hackers, who work ethically within legal boundaries, grey hats operate without explicit permission, often identifying security flaws in computer systems or networks without prior authorization. However, their intent is typically not malicious, differentiating them from black hat hackers who exploit vulnerabilities for personal gain or to cause harm.
While grey hat hackers may uncover weaknesses that can prevent more devastating cyberattacks, they also walk a fine line between ethical hacking and illegal activity. By accessing systems without consent, grey hat hackers sometimes breach cybercrime laws, making their contributions to cybersecurity a double-edged sword.
Many cybercriminals exploit the same types of vulnerabilities that grey hats expose. This creates an ethical dilemma for organizations deciding whether to embrace grey hat contributions or to take legal action against unauthorized access. Some companies have turned to bug bounty programs as a way to legally incentivize grey hat hackers to find and report vulnerabilities responsibly, helping bolster cybersecurity without crossing legal or ethical lines.
Grey hat hackers in incident management
When a cyberattack occurs, the immediate focus of an organization is incident management — identifying, containing, and mitigating the damage. While white hat hackers are often called in to help manage cyberthreats, grey hat hackers may have already uncovered key vulnerabilities that play a role in the attack.
For example, grey hat hackers frequently discover security holes that could be exploited by malware, such as ransomware or Trojans. By reporting these findings — albeit sometimes after accessing the system without permission — they can aid in the prevention of more severe attacks. However, if their actions are not reported through proper channels, organizations could face delayed responses, which might lead to increased damage and data loss during a breach.
Grey hat hackers also inadvertently highlight gaps in an organization’s incident management protocols. Their unauthorized access often reveals security flaws that internal teams may have overlooked, prompting a reassessment of existing cybersecurity measures. While grey hats operate outside traditional incident response protocols, their activities often serve as an informal test of an organization’s cyber resilience.
Frequently Asked Questions
Ethical hackers, also known as white hat hackers, play a crucial role in strengthening cybersecurity. By conducting vulnerability assessments and penetration testing, they help organizations identify weaknesses in their computer systems before cybercriminals can exploit them. Ethical hackers follow legal and ethical standards, ensuring that any vulnerabilities they uncover are responsibly disclosed and promptly fixed.
While grey hat hackers don’t typically engage in outright criminal activity like black hat hackers, they do operate in a legal gray area. By probing systems without permission, grey hats can sometimes cross into illegal territory. If a grey hat hacker discovers a vulnerability but fails to follow responsible disclosure protocols — or, worse, exploits it for personal gain — they could be classified as a cybercriminal in the eyes of the law.
Organizations can protect themselves from both grey hat and black hat hacking by investing in robust cybersecurity measures. These include implementing intrusion detection systems, conducting regular security assessments, and engaging with ethical hackers for penetration testing. Additionally, organizations can establish responsible disclosure policies, which allow white hat hackers and grey hats to report security flaws ethically and legally, reducing the risk of unauthorized access.
Malware can have a devastating impact on computer networks by creating backdoors, stealing sensitive data, or disrupting critical operations. Types of malware, such as ransomware and Trojans, can cripple an organization’s operations, leading to significant financial and reputational damage. Effective cybersecurity measures, such as anti-malware tools, firewalls, and regular patching, are essential to prevent and mitigate the effects of malware attacks.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.