A DDoS Attack Just Breached Your Defenses — Now What?
Additional commentary and subject matter support from Surmed Shaikh
Contents
Introduction
Akamai recently offered insights into the distributed-denial-of-service (DDoS) attack trends of 2024. The most distinct trend was that cybercriminals are pivoting toward highly sophisticated attacks over traditional volumetric or hypervolumetric attacks. While old-school volumetric DDoS attacks that consume vast amounts of bandwidth always draw attention, others with traffic volumes that wouldn’t provoke a yawn have caused devastation in locales around the world.
Observed: Several types of DDoS attacks simultaneously
As with the rest of the security landscape, denial-of-service (DoS) attacks undergo cycles of innovation to continue the mayhem.
Late in 2024, Akamai observed unprecedented campaigns including several types of DDoS attacks targeting businesses and government institutions in the Asia-Pacific region. The attacks were highly sophisticated and ran for several months, across multiple countries in the region, causing CISOs, CIOs, and network security teams to have several sleepless nights.
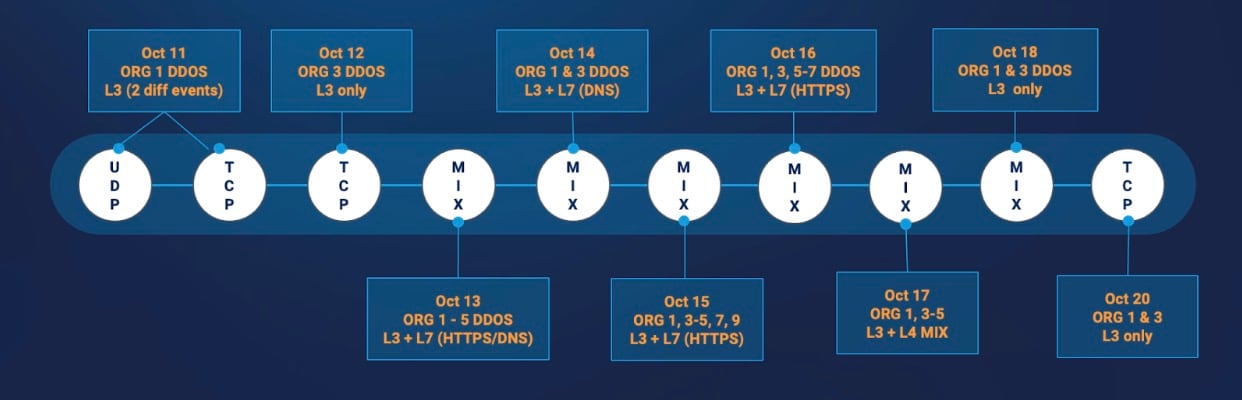
The cybercriminals attacked multiple businesses simultaneously, effectively showcasing the amount of resources available to them for orchestrating sophisticated attacks at scale (Figure).
Moreover, the threat actors rapidly cycled through multiple vectors and used other tactics, techniques, and procedures in what appeared to be a probing strategy to identify the strengths and weaknesses of targeted defenses. They tailored the subsequent DDoS attacks to the specific infrastructure of the victim organizations. This distinct pivot from brute-force DDoS to a more strategic DDoS attack approach alarmed security professionals.
The bad news
Many of the DDoS defense systems that depended on automation only or on-prem only failed, which had a significant impact on several organizations. As organizations and institutions went offline, consumers were often the most affected:
In one instance, airline operations were struck, leading to flight delays and other inconveniences to passengers.
In another, the customers of a financial services firm could not access their accounts.
The limitations of automation-only DDoS platforms were further highlighted when some security teams could not log on to their DDoS protection system consoles to verify or update configurations.
The good news
Customers who were using Akamai DDoS protection solutions based on our platform-people-process framework successfully withstood these attacks. Akamai also provided emergency help to businesses that were adversely impacted because they lacked adequate automated DDoS defense platforms to protect their systems.
When automation-only approaches failed in the face of sophisticated campaigns, Akamai’s recipe of machine automation combined with human intelligence from the global Security Operations Command Center (SOCC) team helped save the day. Robust processes, developed through proactive engagement with expert teams, also helped organizations ensure their winning defense posture.
Sophistication is supplanting scale
The confidentiality, integrity, and availability (CIA) triad is a fundamental concept in the cybersecurity world. Without availability, confidentiality and integrity are stranded — and business is disrupted. This makes DDoS attacks a serious discipline.
Scale can still be a factor, but attackers are investing in sophistication and precision to mimic legitimate network traffic and maximize ROI by:
Using AI to enable better reconnaissance and allow better identification of vulnerabilities and targets to make attacks more efficient and effective. DDoS attacks aren’t happenstance; they’re tailored to each target's digital infrastructure. Attackers are equipped to know as much about your infrastructure as you do, if not more.
Building, buying or borrowing tools and infrastructure, or inducting billions of Internet of Things (IoT) to provide pools of potential to probe for weaknesses or source traffic. IoT device anonymity, diversity, and capacity give them lots of options to build powerful botnets.
Orchestrating everything and incorporating feedback from telemetry to enable variation of target servers and attack vectors, and allow precise routing. This makes multi-vector protocol attacks easier to launch, sustain, and change in flight. Today, 60% of attacks have two or more vectors and the duration is variable.
Cooperating to pool resources and expertise and maximize presence. Different organizations with different objectives — state-sponsored actors, hacktivists, and even script kiddies — can be seen working together in some instances.
Integrating extortion techniques like ransomware and malware into unified DDoS toolsets to improve monetization. This adds economic costs for the victims beyond business disruption and increases compliance exposure.
A sophisticated Asia-Pacific DDoS campaign
The pivot toward sophistication over scale was evident in several DDoS attacks observed by Akamai in 2024. The Asia-Pacific DDoS campaign that we referenced earlier in this blog post had the following characteristics:
Attacks used only modest bandwidth (ranging from less than 1 Gbps to 119 Gbps) but had significant impact by taking victim organizations offline
Multiday attacks were orchestrated to start and stop in 12-hour segments and pick up the next day
Globally distributed bots targeted large numbers of destination IP addresses simultaneously (often in thousands) and took essential customer-facing systems offline
Attack times, vectors, patterns, and volume were all varied in combination with shifting targets, adding complexity to the lives of stressed IT security teams
Numerous attack vectors included, but were not limited to, flood attacks using PSH-ACK, SYN, and UDP; GRE protocol; GET floods; HTTP requests; and DNS reflection, which were used to bring down vital services
TCP-based vectors such as out-of-state packets, which are more complex to mitigate than UDP-based vectors, were also heavily used, which increased the remediation challenge
During the first two days of attack waves, volumetric DDoS consisting of Layer 3 and Layer 4 signatures were the primary multivector focus; application-layer attacks (Layer 7) were minimal
After the first two days of attack waves, Layer 7 HTTP flood DDoS, primarily GET flood requests with diverse URI paths to target critical web applications of major finance institutions, had sharp surges of 2.5 million requests over 2 minutes
Massive Layer 7 HTTP request floods exceeded 180 million requests per second, in less than 30 minutes (Akamai and other organizations have previously reported on botnets capable of sustaining these rates)
As noted, some of the victims of these cyberattacks had purely automated DDoS defenses that were insufficient to deter these sophisticated exploits. Human intervention was required for successful remediation.
It’s unlikely that cybercriminals will relent; in fact, trends observed by Akamai and outlined in this blog post suggest that attackers are working to sustain, and probably build on, their recent successes. Persistence, automation, and leverage equip the attackers to endure.
DDoS protection is a balancing act
DDoS protection services are always a balancing act between permitting legitimate traffic that supports the business and denying unwanted or malicious traffic that taxes bandwidth and infrastructure resources. Today’s focused and optimized DDoS attacks are based on careful surveillance. Vectors, duration, protocol mix, and variable flow rates can be adapted on the basis of telemetry and informed decision-making.
Hackers are systematically testing varied attack surfaces for relative weaknesses before inducting resources to target those specific areas of your digital network infrastructure. Rules and robust processes that mirror attack traffic have to be defined, even as that traffic changes, without impacting the legitimate traffic.
Perfection is hard to achieve and expecting zero downtime is a loss leader in today’s world where any modern DDoS attack is like a zero-day. You don’t know what is going to be sent or what is going to be targeted or at what rates, size, or complexity.
Automation is a useful tool, but it has to be used wisely. Anyone can stop DDoS by overfiltering SYN floods with rate controls, for example, but that will have a negative impact on the business.
Striking the right balance
Striking the right balance requires a bias toward preserving legitimate traffic, starting with signature-based filters aligned with deployed applications and services to ensure consistency. Carefully calibrated rate limiting may be used when needed, and, in some instances, a manageable amount of attack traffic may be permitted.
Akamai’s DDoS protection solutions have always been weighted toward preventing false positives; that is, allowing legitimate user traffic from reaching your origin while preventing DDoS attack traffic. A carefully metered amount of DoS attack traffic can be designed not to overwhelm digital infrastructure.
But even a single instance of preventing legitimate users from accessing resources may impact brand and reputation, or even attract a compliance overview. Informed organizations that internalize this are often reluctant to rely on automation alone.
Taking a structured approach to DDoS attack protection
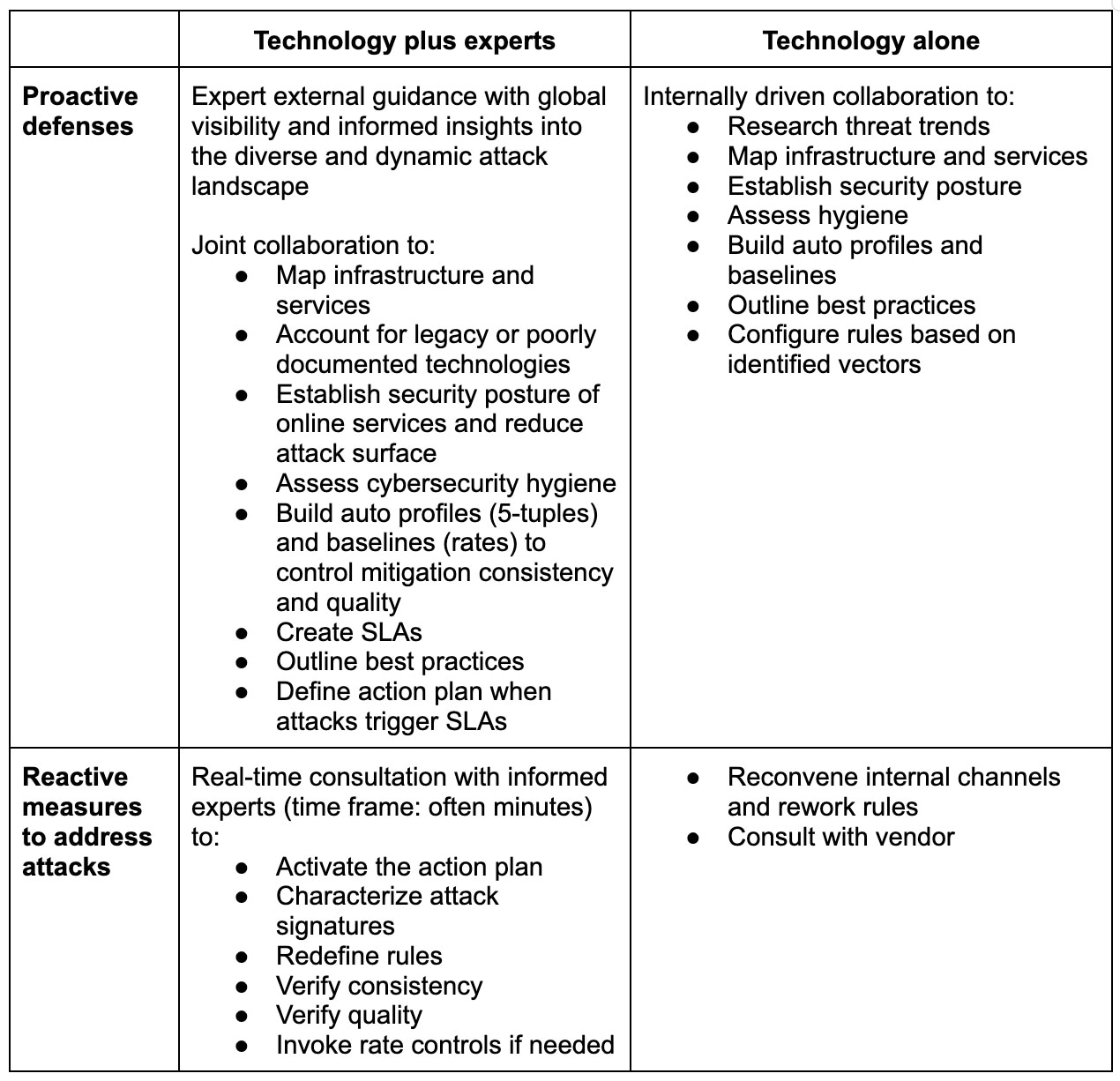
It’s worth considering a structured approach to DDoS attack protection, which incorporates experts who intervene when attacks overwhelm or evade pre-staged defenses. A methodical incident response plan and service-level agreements (SLAs) can deliver the highest possible availability of critical services that support the business (Table).
The two approaches to DDoS protection
Proactive approaches
There are similarities in the proactive section of the two approaches. Both include an upfront effort to understand the IT landscape and formalize deployment of DDoS protections. The key difference is the joint collaboration with experts who have global visibility and informed insights to provide a powerful foundation for the work that follows; i.e., defining more robust defenses.
Reactive approaches
There are distinct differences in the reactive section of the two paths. Joint planning for worst-case scenarios can lead to far more positive outcomes even when attacks mutate in unexpected ways. SLAs create exceedingly strong incentives for defenders to meet them. The power of people is revealed.
For more than 20 years now, Akamai has advocated for the “technology plus experts” approach to keep some of the most important businesses, critical public institutions, and enterprise-grade organizations, across all major industries and all geographies, safe from evolving DDoS attacks. Twenty-plus years of sustained leadership is reflected in our humility and maturity.
People power produces better DDoS outcomes
“Managed” is the new normal for a multitude of internet services today. People always play a critical role in managed services by providing expert interfaces to the services they support. Defenses for DDoS threats shouldn’t be any different. It’s critical to have another layer of defense when automation is insufficient or process lapses create unintended exposure.
A managed service with an SLA that reduces exposure can actually decrease costs — and in highly regulated industries an SLA adds even more value by contributing to compliance mandates.
Let’s take a minute to explore the financial element a bit more. Even if automated DDoS defenses do their job 70% to 80% of the time, the 20% to 30% of cases when automation fails can incur substantial costs. The indirect costs of network security team person-hours spent trying to reboot server resources and bring systems back online can be significant.
Can you determine a precise cost for the hours lost by teams who must work overtime to bring resources back up? Can any experienced organization really put a dollar amount on peace of mind for their digital infrastructure team?
People deliver on SLA commitments — purely automated solutions don’t. People enforce a time to stop. People ensure consistency of mitigation. People draw on deep experience to create rules that permit legitimate traffic and balance it against an agreed percentage of unwanted traffic that won’t adversely impact services and business functions.
DDoS attacks are back, badder than ever — so, what can you do?
DDoS attacks never actually went away — the emphasis just shifted as newer visible and impactful cyberthreats hit the landscape. DDoS innovation continues and decision-makers are reassessing the ROI of defenses, especially as attacks incorporate monetization tools.
Automation is important, but it must be combined with oversight. Informed experts need to intervene to keep online businesses humming when automation or processes fail. It’s also important to explore the total costs of DDoS protection — automation plus SOCC access — and account for the cost of adverse impacts on critical services if a purely automated solution fails.
Akamai’s platform-people-process approach: Automation plus human intelligence
Akamai is lauded for its rapid and comprehensive DDoS mitigation, backed by robust global infrastructure. We’ve had six generations of leading DDoS functionality, and you’ll see much more innovation as we build on our enduring platform-people-process approach to deliver machine automation augmented with human intelligence.
We’re ready to consult with enterprises, service providers, and other organizations to demonstrate why our defenses are superior in the face of today’s sophisticated, dynamic attacks.