Study Reveals API Security Gaps in Asia-Pacific Compliance Programs
Application programming interfaces (APIs) play a crucial role across modern applications and services, enabling seamless communication and data sharing among different systems. Today’s widespread reliance on APIs presents significant cybersecurity challenges that have prompted global regulators to respond.
According to Akamai’s 2025 API Security Impact Study, nearly 9 in 10 enterprises across China, India, and Australia said they factor API security into their data security regulations compliance. (In Japan, the percentage is slightly lower: nearly 8 in 10.) This is good news because enterprises in the Asia-Pacific (APAC) region are increasingly expected to prove they have effective controls for protecting APIs and understanding their risks.
However, Akamai research has also uncovered some bad news.
Less than half of respondents actually include APIs in key deliverables that most mandates require. For example, only 40% and 41% said they factor APIs into reporting and risk assessments, respectively.
This gap comes at a time when 85% of the APAC organizations we surveyed have experienced API security incidents — such as data breaches — over the past 12 months.
Why APIs are a prime attack target
Today’s regulators are seeing what attackers have already learned. APIs are a prime attack target because they are often misconfigured, lack security controls, and are built with vulnerabilities that enable threat actors to steal sensitive data, including personally identifiable information (PII).
In this blog post — part four of our compliance series — we’ll explore findings from the four APAC countries we surveyed: China, Japan, India, and Australia.
China: Gaps among enterprise roles show need for clear, centralized API visibility
Nearly half (48%) of Chinese organizations factor APIs into the security plans that regulators demand as proof they are taking strong measures to protect sensitive data. Although this statistic looks promising, it was skewed by one audience segment’s answers.
71% of C-suite respondents (CISOs, CIOs, and CTOs) believed their organizations include APIs in the plans they send to regulators
In contrast, only 34% of senior cybersecurity pros — whose teams tend to be closer to day-to-day compliance tasks — agreed
Why does this gap matter? APIs are embedded in every application, cloud service, and AI-driven tool an organization builds. They constantly exchange data — and rarely get adequate protection.
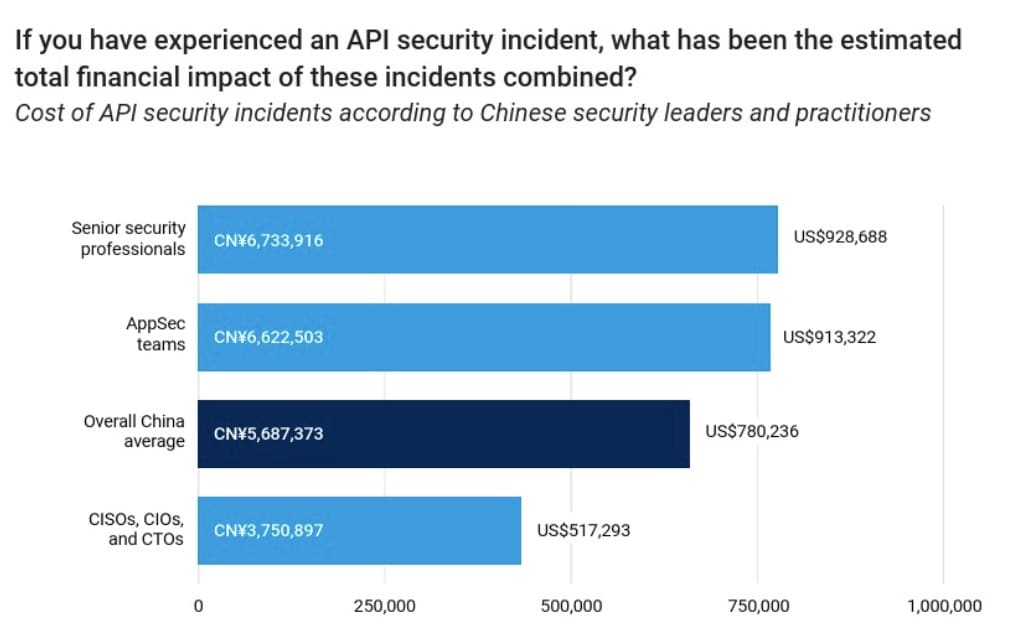
Our study shows how API abuse and attacks are hurting Chinese organizations financially. We asked respondents to estimate the cost of the API incidents that they’ve experienced in the past 12 months, including regulatory fines (Figure). Of note, the cost cited by senior security professionals is 80% higher than the cost cited by Chinese C-suite respondents.
Our research uncovered leader vs. practitioner gaps in other areas, as well.
Although nearly 99% of C-suite respondents said APIs have a place in their regulatory compliance efforts, only 79% of senior security pros agreed
In enterprises with full API inventories, 53% of C-suite respondents said they know which of their APIs return sensitive data — but only 25% of senior security pros agreed
The Data Security Law of the People’s Republic of China requires implementing robust cybersecurity measures to secure the exchange of customers’ PII across systems via technologies like APIs . Here are some capabilities that can provide much-needed visibility, which can boost the security posture of APIs.
Automated API discovery tools: Detect unmanaged APIs (e.g., shadow APIs) that traditional tools like gateways often can’t see
API posture management: Identify which APIs access sensitive data, scan for missing authentication, and alert teams to vulnerabilities
Japan: Not factoring APIs into regulatory requirements can hurt well-earned trust
Japan had the highest percentage of respondents (22%) who said they do not factor APIs into compliance requirements. This was led by 28% of C-suite professionals, whose most common reason was “regulators aren’t asking for it yet.” The problem is that APIs are showing up in Japanese data security regulations.
Japan’s Act on the Protection of Personal Information requires conducting data protection impact assessments to identify and mitigate risks for technologies, such as APIs, that:
- Process large volumes of personal data
- Involve high-risk data processing activities
We asked respondents to rank the top three impacts, or consequences, of the API incidents they experienced. “It hurt our department’s reputation with our senior leaders and/or board of directors” topped the list among overall respondents and ranked nearly 10 percentage points above “fines from regulators.”
Concerns over losing trust among CEOs and board members are merited. In the aftermath of a breach, a company’s leaders want to know how it happened. But this is a difficult question to answer when an organization lacks fundamental insights into API risk.
Only 37% of Japanese enterprises with full API inventories know which of their APIs return sensitive data. That number falls to 8% when singling out Japanese automotive companies, which also:
Experienced the highest cost of all industries — JP¥228,000,000 (US$1,500,000) for API security incidents — more than double Japan’s average
Were among the three most likely of the eight industries surveyed to say they don’t factor APIs into compliance
Given how frequently automakers embed APIs into connected vehicles, it’s important to see risks before they escalate. In this case, it’s helpful to have dedicated API runtime protection capabilities that:
- Monitor for data tampering and leakage, policy violations, and suspicious behavior
- Prevent API attacks and misuse in real time with partially or fully automated remediation
In many regulations, APIs aren’t mentioned by name, but the requirements clearly entail securing the applications and infrastructure within which APIs operate. For example, Japan’s Guidelines of Cybersecurity in the Financial Sector calls for regular assessments to identify and analyze risks, including threats to supply chains.
India: Despite gaps, aligned focus on API misconfigurations can bolster compliance
Half of Indian CISOs, CIOs, and CTOs said APIs are included in their reporting to regulators — but only 29% of AppSec professionals agreed. Even more concerning is the 30-point gap between C-suite pros (57%) and AppSec pros (27%) on whether their enterprises factor APIs into cybersecurity plans.
Fixing these misalignments is critical. India’s Digital Personal Data Protection Act requires cybersecurity mechanisms to detect data breaches, including API breaches, and regular audits, which includes accounting for APIs.
Across regions, we’re seeing that regulators, with guidance from the OWASP API Security Top 10 Risks, are increasingly aware of how threat actors compromise APIs. So when they ask enterprises to demonstrate API security efforts, they’re looking for insights on OWASP-covered threats such as Broken Object Level Authorization (BOLA).
With BOLA, threat actors exploit API endpoints by manipulating object IDs in the API requests they submit. This vulnerability — which often involves misconfigured authorization checks — enables lateral movement. Misconfigurations were the top-cited cause of API incidents experienced by Indian enterprises and the number one cause among Indian financial firms.
But India’s financial industry also provides hope. One hundred percent of surveyed financial firms said they factor APIs into compliance, and a record 72% factor APIs into security plans that mandates require.
There are, however, still gaps. While nearly two-thirds (65%) of Indian C-suite respondents said they believe they know which of their APIs return sensitive data, a shockingly low 11% of AppSec pros agreed. These steps can help:
Build a baseline understanding of normal API behavior through an API posture management tool
Use API runtime protection to identify high-risk behavior and block suspicious traffic before it can access critical resources
Australia: Infrequent API testing during development hinders the ability to assess risk
Australia had the most API security incidents of all surveyed APAC countries, and respondents were mostly aligned on whether they factor APIs into compliance (~90%). However, when it comes to whether they’re factoring APIs into the risk assessments that regulators require, there’s a 21-percentage-point disagreement:
- 54% of AppSec professionals said yes
- 33% of CISOs, CIOs, and CTOs said no
We also noticed this kind of discrepancy in Australian industries. For example, while 82% of auto companies said they factor APIs into risk assessments, only 28% of energy and utilities companies share this practice.
Like many APAC regulations, Australia’s Consumer Data Right emphasizes robust security protocols to protect consumer data during transmission and access. However, it also includes standards to ensure a company’s developers build APIs in a standardized and secure manner. Why is this important? API coding errors — made in the development phase — were the number one cause of API incidents in Australia, according to senior security professionals.
Development teams face pressure to work quickly. This makes it easier for an API vulnerability or design flaw to happen and subsequently go undetected. This points to the need for shift-left API testing (that is, testing that begins earlier in the API’s software development lifecycle) so organizations can spot and address risks before APIs are released into production.
In Australia, the problem isn’t that APIs are not being tested — it’s that they’re not being tested frequently enough. Our study revealed only 6% of Australian enterprises test their APIs in real time. Alarmingly, no companies (0%) in API-rich sectors like financial services, healthcare, and manufacturing are testing their APIs in real time.
How can you address this? Look for tools that can:
Inspect API specifications against established API governance policies and rules
Perform regular outside-in attack simulations — based on real-world threats — to discover and assess API risks
Key takeaways: Stronger API security can boost compliance efforts
Our research shows that APAC organizations are increasingly aware of threats to the APIs that are powering their applications, cloud services, and AI innovations. But securing these APIs remains a struggle. It is essential to bridge the gap between recognizing API security’s important role in compliance and actually implementing API security in key regulatory deliverables.
By understanding API attacks’ root causes, impacts, and priority levels, enterprises will be in a better place to protect themselves — and to show regulators that they’re taking all measures to secure their data. You can read the full 2025 API Security Impact Study for more insights.
Learn more
In this blog series, we’ve explored common compliance challenges and discussed best practices for solving them with comprehensive API security.
Check out our cybersecurity compliance page to learn about four key areas of security that can improve your ability to meet regulators’ requirements. You’ll also find insights on how Akamai helps organizations comply with mandates, and stories about how our customers strengthened their approaches.