Contents
Introduction
In this blog post, we’ll explain what DNS hijacking is, what types and techniques cybercriminals use, and how to protect DNS servers from this attack. This should help you understand the threat of DNS hijacking and determine which cybersecurity measures you need to prevent your DNS servers from being compromised.
To understand DNS hijacking, you must first understand the ins and outs of DNS. Let’s start there.
What is DNS?
DNS stands for Domain Name System. You can think of DNS as a phone book for the internet. Essentially, it's a protocol that turns human-readable domain names (like www.akamai.com) into computer-readable IP addresses (sets of four numbers separated by periods).
The human brain can’t memorize strings of numbers quite as easily as computers can, so we created domain names for each website that correspond to the IP addresses.
Each domain and its corresponding IP address for every website is held by an authoritative nameserver somewhere in the world. The process of retrieving that information — to connect a user to their desired website — is known as DNS resolution.
What is DNS hijacking?
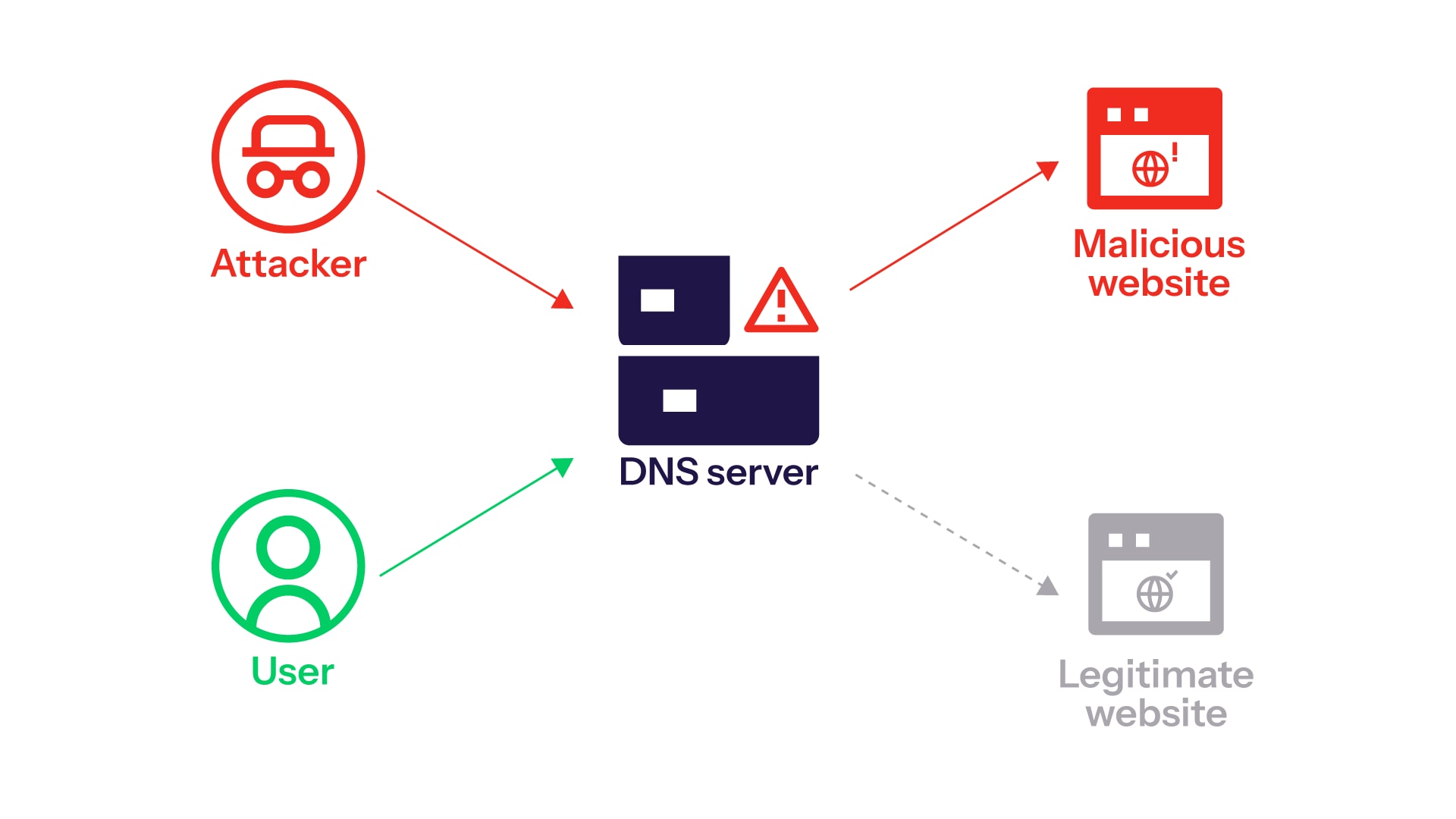
DNS hijacking is a type of cyberattack in which a cybercriminal directs traffic to an imposter site in an attempt to steal sensitive information by exploiting DNS resolution.
How normal DNS resolution works
Here’s how a normal DNS resolution works:
A user enters a domain name (like www.akamai.com) into the browser’s address bar, initiating a DNS request. The end user’s machine sends the query to a nearby DNS recursive resolver.
A DNS resolver acts as a middleman between the user’s device and the nameserver that will provide the IP address. These resolvers often belong to internet service providers (ISPs) and improve performance by caching DNS records closer to the source of the query and removing unnecessary steps to retrieve the answer.
Each DNS resolver hosts a cache of recently resolved IP addresses and their respective domain names. If the queried hostname is in the cache, then the resolver will return the record directly. If not, it will contact the necessary nameservers belonging to the Domain Name System’s distributed, hierarchical database to discover the IP address.
More specifically, the resolver will read the domain from right to left, as each “period” typically represents a different “zone,” and each zone will delegate the request until the authoritative is queried.
For a lookup for www.akamai.com, the resolver will query a “root” nameserver, which will delegate the request to the “.com” zone. Finally, the .com zone will refer the request to the akamai.com domain space that will return the IP address for the www subdomain. The resolver will cache all of this information and return the IP address to the client.
Once the IP address has been returned, the user’s device connects to the website. Usually, this entire process occurs within milliseconds.
Watch this video to learn more about the basics of DNS and recursive and authoritative servers.
How a DNS hijacker disrupts normal DNS resolution
A DNS hijacker disrupts this process. During a DNS hijacking attack, a device user generates a query that is then answered not with the legitimate IP address for the website they were attempting to visit but instead with a malicious site or malware designed to steal data (Figure 1).
The need for DNS security
Because DNS is an essential component of using the internet, DNS security is a crucial aspect of a comprehensive cybersecurity program. DNS hijacking can have devastating consequences — from financial losses to eroded trust between your organization and its customers.
The number of internet-connected devices in our world is constantly growing. At the same time, cyberthreats are becoming increasingly sophisticated. Strong DNS security can protect your organization from internet disruptions, costly data loss, and broken trust.
What causes DNS hijacking?
As is the case with many types of cyberattacks, DNS hijackers often carry out their attacks by exploiting security vulnerabilities within DNS infrastructure.
Hijackers often target weaknesses like outdated firmware or default passwords to gain access to routers to change their DNS settings. Other attackers exploit vulnerabilities within DNS servers — such as outdated software or caching mechanisms — to gain control of the servers and point users to malicious sites.
Phishing is another common source of DNS hijacking. In this type of DNS attack, hijackers trick unsuspecting victims into downloading malware that alters their local DNS settings.
For instance, a hacker might impersonate a trusted individual or organization in an email, urging the recipient to click on a link they claim leads to a legitimate website. In actuality, if the recipient opens the link, malware is downloaded and their system is compromised.
Exploring types and techniques of DNS hijacking
There are many different types of DNS hijacking, each with its own unique characteristics and scope of potential damage. Some of these include:
Local DNS hijacking
Router DNS hijacking
Machine-in-the-middle (MITM) attacks
Local DNS hijack
One common type of DNS hijacking is a local DNS hijack. In this type of attack, a hijacker installs malware onto an individual user’s computer to change their local DNS settings and gain access to data. The malware, sometimes called a Trojan, is unknowingly downloaded by a user through a suspicious link from a pop-up or phishing scam. In a local DNS hijack, only one device is affected.
Router DNS hijack
Another common type of attack is a router DNS hijack. In this attack, the hacker takes advantage of vulnerabilities in a router to access the ability to change its DNS settings. For example, the attacker could configure a compromised router to direct queries to a malicious DNS server that ultimately points users to an imposter endpoint.
Machine-in-the-middle attacks
Another type of hijack that can impact multiple devices and users is a machine-in-the-middle (MITM) attack. In this type of attack, a hijacker intercepts DNS communication between a user and the DNS server they’re querying, replacing legitimate query resolutions with malicious IPs.
DNS spoofing vs. hijacking: Understanding the difference
DNS spoofing, sometimes called DNS cache poisoning, is another common type of DNS attack, but it differs from hijacking in a few key ways. In DNS spoofing, an attacker manipulates DNS records stored in the cache of a particular DNS resolver, injecting false information that creates fraudulent responses to DNS queries.
Once false IP addresses are added to a cache, a user’s DNS queries take them to fake websites that in many cases appear to be nearly identical to their legitimate counterparts.
Both spoofers and hijackers exploit DNS systems to gain access to sensitive information. The main difference is that while spoofers change cache records, hijackers aim to direct DNS queries to a malicious DNS server by modifying DNS settings on a victim's device or router, or by intercepting and manipulating live DNS traffic.
Since DNS caches tend to expire every few hours or days, spoofs can only last so long. DNS hijacks, however, often last longer and can have more devastating consequences.
The threat of DNS hijacking in today's cyber landscape
How common is DNS hijacking?
As cybercriminals become more sophisticated in their methods and the number of internet-connected devices grows, cyberattacks like DNS hijacking will likely become even more common in the coming years. A strong cybersecurity posture is, therefore, an absolute necessity.
In a study from Palo Alto Networks’s Unit 42, researchers analyzed 29 billion new DNS records from March to September 2024. The researchers flagged 6,729 of these records as DNS hijacking, which is an average of 38 DNS hijack records per day.
Some high-profile DNS attacks have made global headlines. In early 2019, Cisco’s Talos security division discovered that a team of DNS hijackers were able to compromise the domains of 40+ organizations, including several country-code top-level domains of various nations.
DNS attacks unveiled: Common characteristics to look out for
Understanding how to recognize a DNS attack is essential to minimize risk of a prolonged exposure. Here are a few ways to recognize a rogue DNS server or DNS redirection:
You’re experiencing a notable slowdown on your device. Legitimate query resolutions typically happen in an instant. When a cybercriminal attempts to redirect your search to a fake website, they must add steps to the query resolution process.
When you type a domain name into your search engine or directly into the address bar, you’re taken to an unfamiliar or suspicious-looking site. If you typed the correct domain name into your web browser but landed on an unfamiliar webpage, it’s possible you’ve been redirected to an attacker’s site.
Another important way to defend yourself from DNS hijacking attacks is to stay alert in the face of phishing scams. If you receive a communication that seems suspicious in any way, proceed with caution and do not open any links included in the communication. For more information about phishing, including tips on how to identify and avoid it, read this article.
Protect your network: Strategies to prevent DNS hijacking
Fortify your DNS infrastructure against cybercriminals
One key strategy for defending your network from DNS hijacking is to fortify your DNS infrastructure. Here are a few ways to do this:
Change your local default DNS settings and router login credentials. Many routers and DNS software come with default settings and passwords. Changing these can help prevent hijackers from gaining unauthorized access to your network.
Implement Domain Name System Security Extensions (DNSSEC) for DNS response authentication. DNSSEC is a protocol that verifies DNS responses for authenticity. It’s an added layer of security that prevents hijackers from modifying or tampering with DNS data.
Invest in advanced security measures to safeguard your DNS
The effects of a DNS hijacking can be devastating. Beyond having potential financial and legal consequences, a data breach can also erode trust between your company and your customers, causing you to lose out on future business.
By investing in advanced security measures, you can greatly reduce the risk of an attack and increase the protection from data theft for yourself, your customers, and your entire organization.
Here are a few advanced measures to consider taking:
Use a VPN to secure your internet searches. A VPN encrypts your internet traffic, allowing you to use the internet more securely.
Use antivirus software to protect your network and devices from malware and malicious websites. Antivirus software works to identify and remove malware, spyware, and viruses from your devices. By securing your internet use and your devices, VPNs and antivirus software work in tandem to provide you with comprehensive digital security.
Engage in regular DNS firmware and server updates. Make it a regular practice to update your router passwords and DNS servers, and to add cybersecurity patches whenever needed. By making these regular updates, you reduce the number of vulnerabilities within your DNS infrastructure that hijackers can use to gain access to your data.
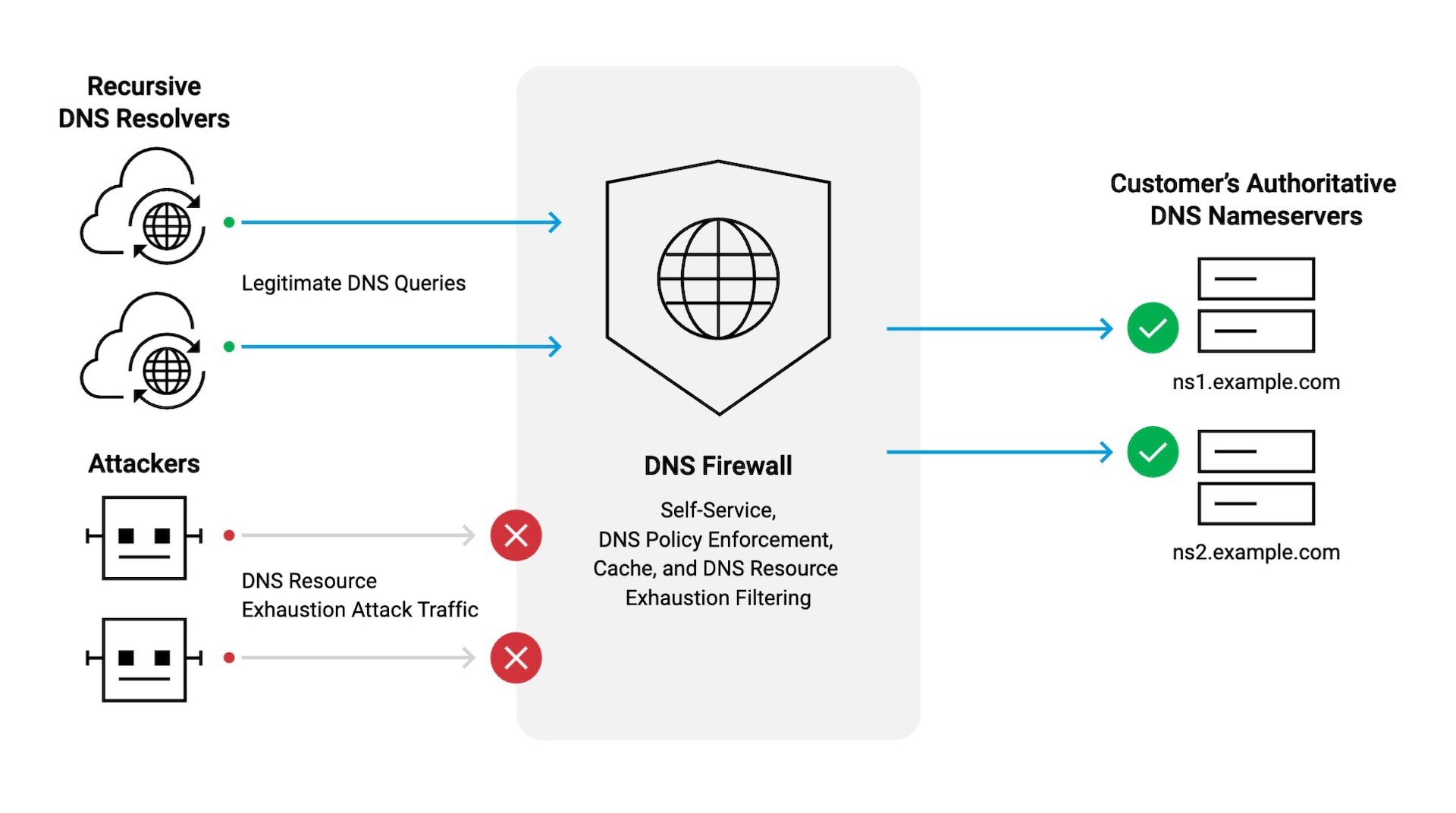
- Set up a DNS firewall. DNS firewalls can block requests to domains known to be malicious and protect devices from navigating to harmful websites. Figure 2 illustrates how it works.
Investing in strong DNS security measures like firewalls can have huge payoffs. In a study from the Global Cyber Alliance, researchers analyzed 11,079 confirmed data breaches. The researchers found that DNS firewalls could have mitigated one-third of the breaches. Moreover, had firewalls been in place, they could have saved the compromised organizations more than US$10 billion in losses.
Secure your DNS with Akamai
Akamai is at the forefront of DNS security, protecting organizations from costly cyberattacks through industry-leading security solutions, superior threat intelligence, and global operational support.
Protect your organization from hijacking and ensure a high level of DNS performance, resiliency, and availability with Akamai Edge DNS. Edge DNS is an intelligent platform that provides comprehensive protection from a wide range of DNS attacks on your DNS infrastructure, whether in the cloud, on-premises, or hybrid.
The highly scalable and flexible platform allows you to self-configure and manage your DNS zones to create and enforce your own policies in real time. It also optimizes the responsiveness of your DNS infrastructure, improving performance and end-user experience.
In addition, with Akamai DNS Posture Management, Akamai now offers a comprehensive DNS observability tool that provides a unified, single interface for all zones. DNS Posture Management:
Highlights any record misconfigurations in real time
Evaluates an organization’s post-quantum compute readiness
Alerts administrators to any inconsistencies with National Institute of Standards and Technology (NIST) and Payment Card Industry (PCI) standards
Users can also review all zone records and evaluate any new DNS updates to ensure all were sanctioned by authorized users.
Staying one step ahead of DNS hijackers
DNS hijacking, an attack in which internet users are redirected to harmful sites, can have devastating consequences. Not only can falling victim to a DNS hijacking have financial consequences — it can also impact your organization’s integrity, eroding trust between you and your customers.
As DNS hijacking becomes increasingly prevalent and sophisticated, it’s more important than ever to have a strong DNS cybersecurity posture.
Informed end users and website owners can help prevent DNS hijacking from occurring. By staying aware, fortifying your DNS infrastructure, and investing in advanced network security measures, you can secure sensitive data and avoid costly hijacking.
Investing in a comprehensive DNS security solution like Akamai Edge DNS can help you protect your organization and your customers from these increasingly large, frequent, and sophisticated attacks.
Tags