| If your organization is under attack right now, our security experts are here for you 24/7. If you need emergency help, please contact us. |
Executive summary
Since 2024, distributed denial-of-service (DDoS) attacks have become highly sophisticated.
Multi-vector, multidestination, and AI-powered DDoS attacks probe existing defenses, identify weak points, and then orchestrate attacks that disable the DDoS defense solution — resulting in a distributed denial of defense (DDoD).
Volumetric DDoS attacks, which are simple and often single vector, are easy to mitigate with self-serve, purely autonomous solutions.
Sophisticated DDoS attacks are almost never high in volume. These types of attacks require a mature DDoS defense solution that is complemented by the intelligence of security experts and a strong network security posture.
DDoS defense platforms that share resources and capacity with content delivery networks (CDNs) and other security solutions often fail in the face of sophisticated DDoS attacks.
- Network security professionals must benchmark their current security posture against the DDoS defense maturity model and explore ways to elevate their security further.
There is a real divergence happening in the distributed denial-of-service (DDoS) attack landscape. On one hand, some vendors are regularly reporting headline-grabbing DDoS attacks that are often simple, single-vector, easy-to-mitigate attacks like UDP floods. Are these attacks high in volumetric terms? Yes, of course!
On the other hand, well-resourced cyberthreat actors are using botnets powered by artificial intelligence (AI) and the internet of things (IoT) to orchestrate highly sophisticated DDoS attacks. Note the key word: “sophisticated.”
That has been the flavor of modern DDoS attacks. These are often multi-vector, multidestination (multiple IP addresses) DDoS attacks, and they use AI-enabled tools to probe your defenses, identify weak spots, and launch an attack that often disables the DDoS protection solution itself, before taking your digital infrastructure offline.
We have entered the era of distributed denial of defense (DDoD).
Protection that is unavailable is meaningless
Over the past few years, there has been a significant increase in the number of high-volume attacks that are highly sophisticated in nature.
In fact, nine of the largest volumetric DDoS attacks mitigated by Akamai Prolexic’s DDoS protection platform took place in the past 36 months. These attacks were often multi-vector, multi-destination attacks that had the potential to overwhelm many rudimentary, autonomous-only or on-prem DDoS solutions in the market.
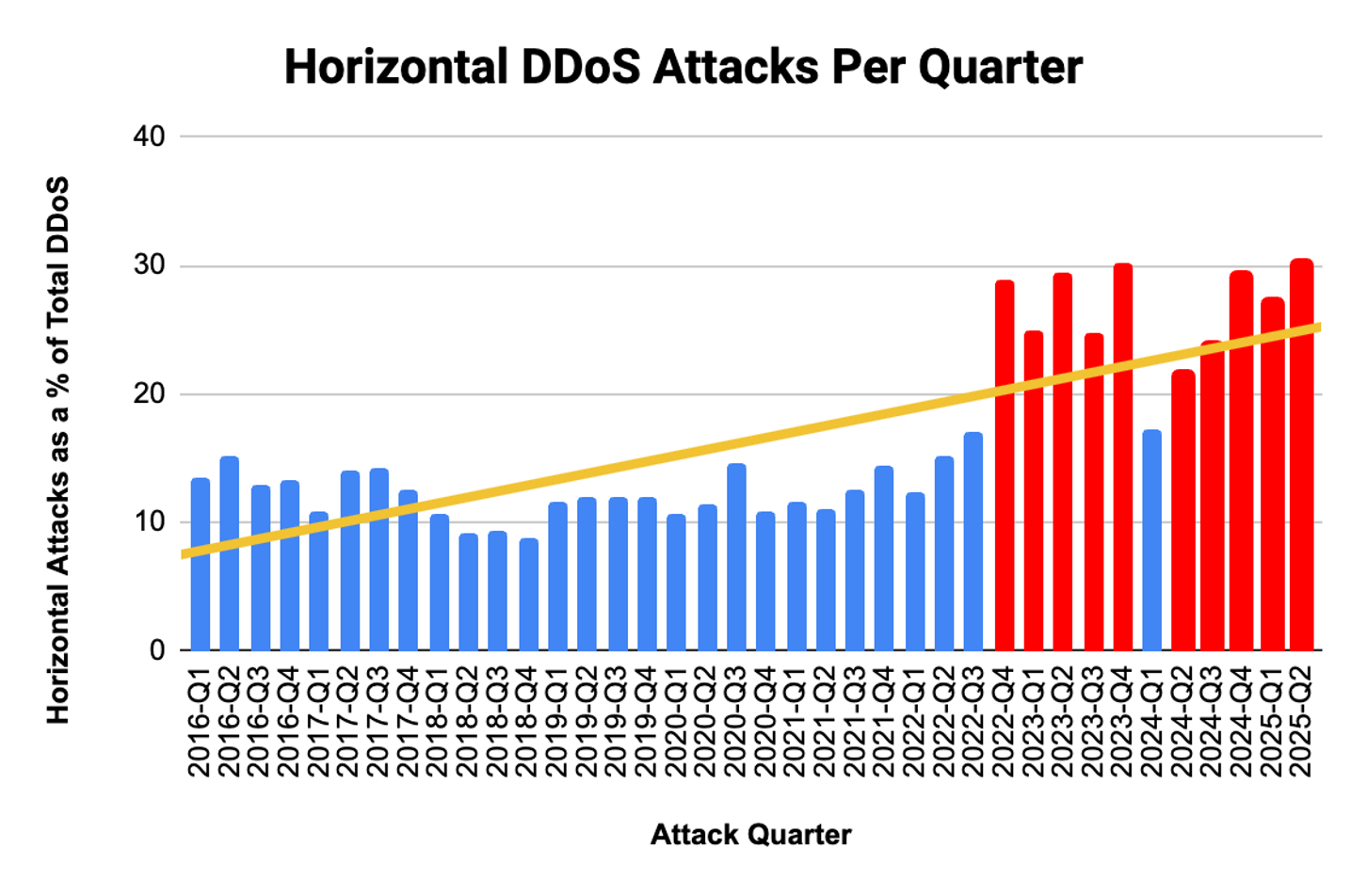
If we look closer into the DDoS threat intelligence collected by Akamai, more than 30% of the DDoS attacks mitigated by Prolexic in Q2 of 2025 were sophisticated and horizontal (Figure 1).
Such sophisticated DDoS attacks require a sophisticated defense approach that combines the power of modern automation, human expertise, and collaboration among the security teams of an organization and the solution provider. This is where Akamai’s platform-people-processes framework offers robust network security posture.
Can your current DDoS solution actually protect you from modern DDoS attacks?
Simple, easy-to-mitigate vectors like UDP floods can be easily blocked by any rudimentary DDoS protection solution. No matter how many terabits per second (Tbps) of attack traffic is generated by an attacker. In many cases, even a simple access control list (ACL) can do the job. These types of simple tactics, techniques, and procedures (TTPs) are hardly anything new or noteworthy to network security practitioners.
An entirely different story are AI-enabled, sophisticated DDoS attacks that intelligently probe your defenses, identify weaker points in your security posture, and then launch a moderate-volume but complex mix of attack vectors. These attacks take your DDoS defenses down and then take your network offline.
We reiterate this particularly important process because DDoS is not a happenstance. A majority of DDoS attacks occur when someone deliberately attempts to flood your network with malicious traffic that saturates your origin’s capacity and prevents legitimate users from accessing your services.
In a few instances, there could be a denial of service (DoS) because of a misconfiguration, a network probe, or an aggressive vulnerability scan. With AI-enabled and assisted tools, cybercriminals can probe your network to detect which part is relatively vulnerable, and then they can concentrate the attack accordingly.
Sophisticated DDoS attacks do not need to rely on volume
Sophisticated DDoS attacks are almost never high in volumetric terms. That’s because the attacker doesn’t have to generate a lot of traffic if it can overwhelm your defenses with a relatively moderate amount of carefully crafted malicious traffic.
Think of it this way: If someone were trying to break into your house, they could either use brute force to break through the front door, trigger the home alarm system, and be prepared to confront the police … or they could identify how to disable your security system and then use a moderate level of effort to break in.
Some of the modern DDoS attacks use the second technique: They disable your security system and then break into your network.
Customer networks often have different levels of redundant capacity or technology built-in so as to absorb or shunt the initial blow of an attack. Unfortunately, that’s not enough.
Controls or devices such as stateless firewalls, for example, can help initially but often have finite capacity to absorb protocol misuse and/or to distribute load equally while also concentrating on servicing legitimate hosts or users. Sometimes all an attacker needs is just enough attack capacity to bring down infrastructure and bypass automated controls.
A clear evolution of attacker capability, resources, and intent
A June 2025 report from FS-ISAC and Akamai, From Nuisance to Strategic Threat: DDoS Attacks Against the Financial Sector, highlights this trend in a detailed manner.
The report says, “Indeed, the most effective DDoS campaigns in 2024 were characterized by strategic reconnaissance and agile execution rather than simple volume.
“In 2024, threat actors increasingly employed advanced multi-vector DDoS strategies that incorporated systematic probing and adaptive tactics. This demonstrates an ability to analyze defenses in real time and dynamically adjust methods to evade automated protections. This marks a clear evolution in attacker capability, resources, and intent, and increases the threat of DDoS attacks against the financial services sector.”
An example
In the final three months of 2024, more than 20 individual financial institutions in the Asia-Pacific region were impacted by an unprecedented and highly sophisticated DDoS attack campaign. Cybercriminals used a multitude of vectors at relatively low volume to skillfully probe and test the true level of DDoS defenses at these institutions.
Despite the moderate volume of attack traffic, the complex mix of vectors and destination IPs led to the failure of multiple purely autonomous and on-prem DDoS protection services, resulting in days of notable and expensive impact on end users.
It is important to note that the attack traffic volume was significantly below the advertised capacity limits of most DDoS mitigation solutions. Additionally, once the fully autonomous and self-service DDoS defense platforms were overwhelmed, customers could not even log on to these platforms to take any action. No network security personnel ever wants to feel this vulnerable and helpless.
The new era: Distributed denial of defense (DDoD)
Over the past few years, Akamai has closely observed this emerging trend of cybercriminals pivoting from the old game of distributed denial of service to the new sport of distributed denial of defense. The attacks in the Asia-Pacific region cemented this transition.
Once your automated DDoS defense system is down, the attacker does not need a high volume of malicious traffic to disrupt your network.
In the Asia-Pacific example, this approach allowed the attacker to successfully attack and disrupt multiple companies at the same time and over weeks. They used the “firing power” of their botnets in an economically efficient way, rather than exhausting their resources with conventional massive-size attacks.
The good news
Akamai Prolexic, our DDoS defense platform, comfortably defended customers from these attacks. One key reason is that we anticipate the failure of “automation only” in our design — there is always a global team of Security Operations Command Center (SOCC) experts monitoring attacks and working directly with the customer.
Our experts are people who fight DDoS attacks every day and have an arsenal of tools to deploy should an attack manage to overcome parts of the automated defense mechanisms.
In fact, Akamai regularly receives outside requests for emergency DDoS protection from organizations whose fully autonomous DDoS defenses were tricked by an attacker. More often than not, vendors that are dependent on fully autonomous defense systems offer neither a backup plan nor any access to human intervention, emergency consultation, or support resources.
The importance of the “availability” of your DDoS defense
A security system is only as good as its ability to defend your network at the time of an attack. Any system that regularly experiences outages, goes offline, or can be easily overwhelmed by a sophisticated attack is completely pointless, no matter how large their “marketed” defense capacity.
In the modern era of sophisticated DDoS attacks, it is relatively easy to overwhelm or completely disable purely autonomous DDoS defense platforms. This is particularly true when the DDoS defense capacity of such a platform is a shared resource with other services, including content delivery network (CDN).
A strategy that Akamai customers have grown to adopt is this idea of diversifying. Having purpose-built, multicloud architectures allows network security personnel to diversify their DDoS defense and avoid the risk of systemic issues across a single platform.
Meeting the minimum requirements is not enough
Many enterprise-grade organizations and institutions in some of the highly regulated industries require a dual DDoS vendor strategy.
In fact, many enterprise-grade customers choose a “good enough” second supplier to meet the diversity requirements but use a proven and well-engineered solution to protect their critical assets. The other assets, often including vanity domains, Q&A environments, and other noncritical functions, are reserved for the lower-cost solution.
We understand that any technology-based solution can experience unintended outages and thereby impact customers; we, too, have experienced outages in the past. But to what extent are you willing to place key or critically defined network assets behind a DDoS solution that may not be available when you experience an attack?
If 40% of your end users are unable to access your services but the DDoS mitigation provider claims that the internet-facing service is up, is that a reasonable outcome? The answer is a solid no.
Is your DDoS defense a shared desk or a full office building?
Some companies brag about having “a dozen meeting rooms, a dozen offices, and a dozen lounges.” Sounds impressive … until you find out it’s just the same hot desk in a coworking space that is being endlessly repurposed.
That’s how pooled DDoS capacity works: One space is stretched thin across every need. Real protection is like a full office building: dedicated floors, conference rooms, and offices that can all operate at once without crowding one another out.
Some DDoS defense vendors advertise the total capacity of their network shared between all defensive capabilities as well as their CDN. The questions that network security professionals must ask are:
How much of this “total capacity” is truly available for DDoS defense when an attack takes place?
If a point of presence (PoP) is already saturated with legitimate traffic, can your defense truly handle a DDoS attack?
Akamai’s dedicated and specialized infrastructure for DDoS defense
We believe that dedicated and specialized infrastructure for DDoS defense provides better reliability, fewer points of failure, and less risk overall. We combine this approach with advanced automation, and a SOCC full of experts to tune and optimize defenses for the individual customer and to help fight attacks even when they aim to trick the algorithms.
Akamai offers a multilayered, multicloud, segmented, and dedicated defense against sophisticated DDoS attacks. For example:
Akamai Prolexic offers dedicated defense against Open Systems Interconnection (OSI) model Layers 3 and 4 DDoS attacks.
Akamai Edge DNS and Akamai Shield NS53 offer dedicated defense against DNS-focused DDoS attacks.
Akamai App & API Protector offers dedicated defenses against Layer 7 (application-layer) DDoS attacks.
Furthermore, Akamai’s edge network automatically drops DDoS traffic even before the other security systems come into play. And Akamai Guardicore Segmentation helps prevent cybercriminals from penetrating your network with ransomware while using DDoS attacks as a convenient smokescreen. In short, Akamai offers comprehensive network security across all ports and protocols.
How to protect your organization in the current DDoS landscape
For some time, there has been an impression that DDoS attacks are old school and DDoS defense has become a minimum requirement. To a certain extent, this idea was true some 5 to 7 years ago, when a baseline level of DDoS defense was offered by most mature cybersecurity solution providers.
However, over the past 3 or 4 years, the DDoS attack landscape has significantly changed. DDoS attacks have become incredibly sophisticated thanks to:
The proliferation of AI-powered tools
Geopolitical events that give rise to well-resourced hacktivists
The easy availability of DDoS-for-hire services
The advent of the always-online world in which businesses and institutions just cannot afford to go offline
It is in this environment that cybercriminals have adapted their TTPs to orchestrate sophisticated DDoS attacks that probe and disable DDoS defense systems and then take their victims offline.
5 steps to take to defend against a DDoS attack
As a network security professional, what recourse do you have? You can start with these five steps.
Develop a robust network security posture that is underlined by proactive detection, behavior-based analysis, and an intelligent combination of automation and human interventions. Relying solely on automated defenses only puts consistency and the quality of mitigation at risk.
Understand attacker behavior and build a baseline for rapid mitigation. Are attackers probing for API vulnerabilities or bypassing application-layer defenses? Is there unusual and irregular request activity from spoofed or untrusted sources? These might be leading indicators of a sophisticated DDoS campaign.
Adopt a DDoS defense platform that has dedicated defense capacity — not shared capacity — and does not have a track record of becoming repeatedly unavailable. Is there a SOCC team available to complement automated defenses? Don’t let an autonomous DDoS defense platform itself become a single point of failure. And, while we're discussing capacity, be sure to look beyond the headline numbers and determine what types of attacks are being reported.
Ensure that your incident response plan is up-to-date. This plan should include a crisis response team with clearly defined roles, communication channels, and predefined strategies for mitigating a DDoS attack.
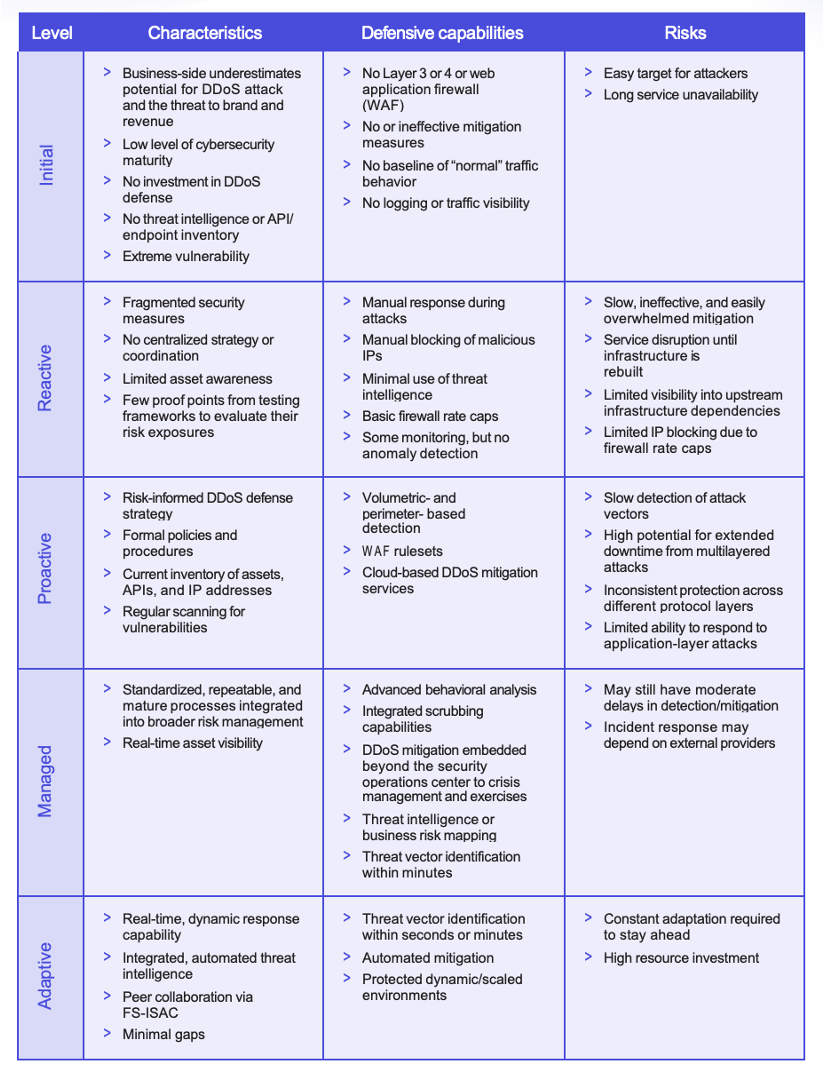
Benchmark your current network security posture against the DDoS defense maturity model developed by FS-ISAC and Akamai, and identify improvement areas to mature your security (Figure 2).
7 steps to take during a DDoS attack
1. Assess your risk and current defenses. Begin by evaluating your current DDoS mitigation capabilities. Are your existing defenses sufficient to handle the size and scope of the attack? Engage with your DDoS mitigation provider to assess the ongoing threat and respond quickly to any vulnerabilities.
If you need emergency onboarding to the Akamai Prolexic DDoS defense platform, contact our security team immediately. |
2. Review your critical IP spaces and subnets. Ensure that your most vital network resources, including critical subnets and IP spaces, are protected by mitigation controls. This will help to limit the areas of your infrastructure that can be compromised by the attack.
3. Activate always-on DDoS security controls. Deploy always-on security controls as a first layer of defense. This proactive approach minimizes the burden on incident responders and reduces the risk of emergency integration scenarios during a crisis.
4. Implement an edge-based cloud firewall. Expand your defenses beyond traditional DDoS protection by deploying an edge-based cloud firewall, such as Akamai Prolexic’s Network Cloud Firewall. This additional layer of security helps to block malicious traffic before it even reaches your network, which reduces the load on your internal firewalls and systems.
5. Protect your DNS infrastructure. Domain Name System (DNS) attacks are a common and highly effective method of disrupting services. Use a robust DNS solution like Akamai Edge DNS to protect against DNS-focused attacks, and deploy Akamai Shield NS53 as a dynamic proxy to safeguard on-premises or hybrid DNS infrastructures.
6. Activate your incident response plan. Executing your well-rehearsed playbook is key to maintaining calm and responding efficiently during a crisis.
7. Extend your protection to application and API layers. Many DDoS attacks target applications and APIs, making it essential to secure these components as well. Akamai App & API Protector offers a web application firewall (WAF) that blocks malicious HTTP requests and safeguards your applications from complex DDoS attacks that target ports 443 and 80.
Learn more
Contact an Akamai expert today to learn more about our comprehensive security solutions.
Tags