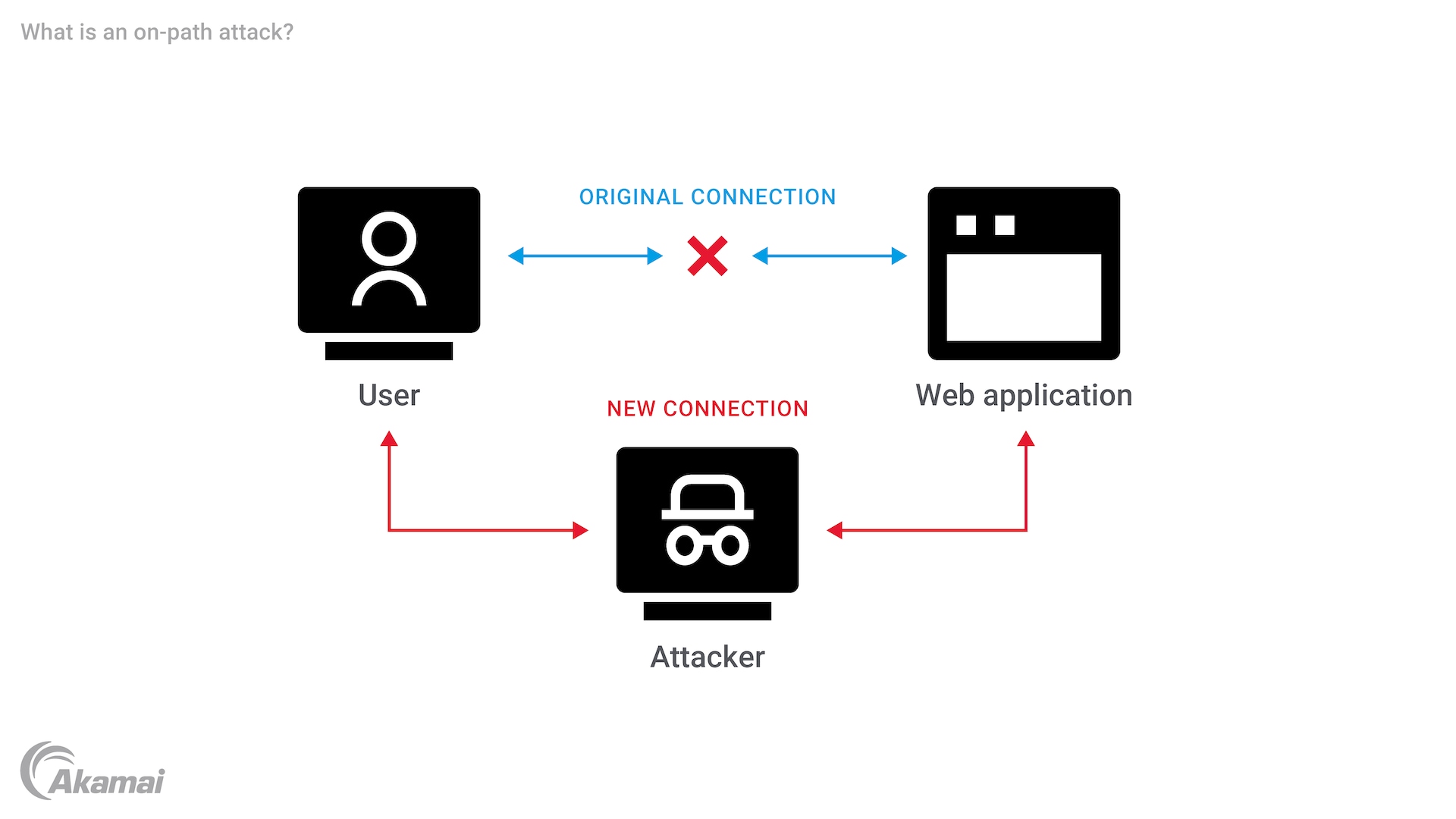
Identifying an on-path attack requires vigilance for anomalies in network behavior. Common signs include sudden drops in network performance, unexpected redirections of traffic, or unauthorized access alerts triggered by suspicious activities. An on-path attacker inserts themselves into the communication path between two parties, intercepting and altering data.
This manipulation can lead to data theft, eavesdropping, or the injection of malicious content. Mitigate the impact of such attacks by recognizing all of these signs promptly. Understanding this type of attack vector empowers your organization to bolster defenses against on-path attackers and safeguard sensitive information.