REST handles authentication through standard HTTP mechanisms like bearer tokens, API keys, OAuth, and JWT (JSON Web Tokens). In contrast, gRPC employs a more extensible and protocol-based approach, using Transport Layer Security (TLS) for secure communication and allowing custom authentication mechanisms. While REST depends on HTTP/1.1 and is typically text-based, gRPC employs HTTP/2, allowing for binary data transfer.
Frequently Asked Questions
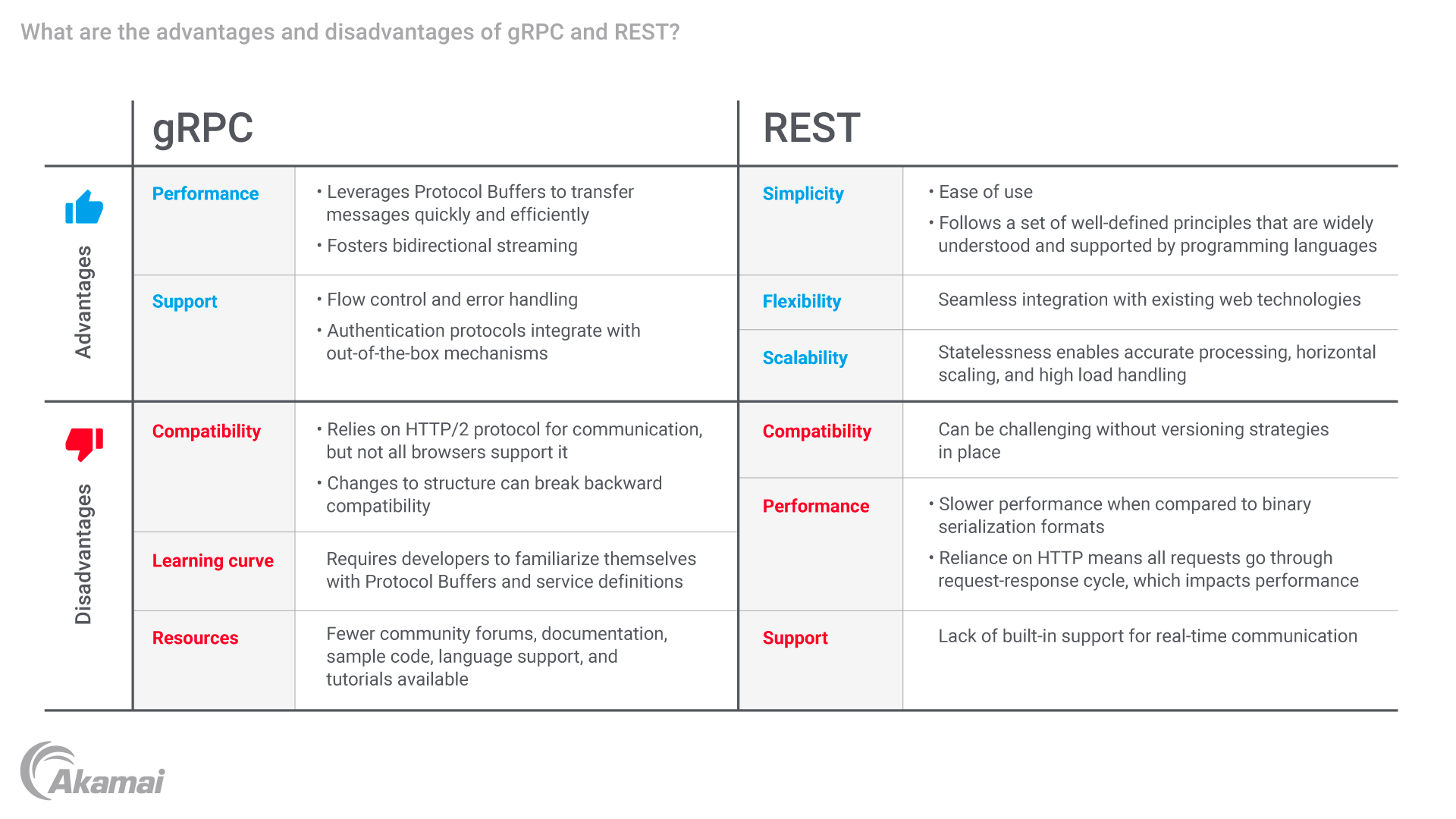
When comparing gRPC vs REST, choose REST in scenarios prioritizing simplicity, like public APIs where ease of use is crucial. REST is preferable for browser-based applications or those requiring broad client compatibility due to its widely supported, human-readable format. Opt for REST when integrating with existing systems already utilizing RESTful APIs, as it ensures compatibility and seamless interoperability.
However, when performance and efficiency are paramount, gRPC excels with its binary data transfer and HTTP/2 support. For robust API security testing tools, consider solutions that meet the specific requirements of either REST or gRPC protocols.
Yes, gRPC and REST can coexist within the same application. Despite their distinct communication paradigms, developers can strategically leverage each approach based on specific use cases or services.
gRPC’s efficiency suits performance-critical tasks, while REST’s simplicity and broad compatibility make it suitable for other functionalities. This flexibility enables a pragmatic approach, utilizing the strengths of gRPC and REST to create a well-rounded and efficient application that meets diverse communication requirements. The key lies in thoughtful integration, ensuring seamless interoperability between the two paradigms within the application.
RESTful APIs have enjoyed widespread adoption, firmly establishing their presence in the industry. However, gRPC is rapidly gaining popularity, particularly in performance-sensitive environments and microservices-based architectures. The well-established nature of REST makes it a default choice for many scenarios. Still, gRPC’s efficiency and modern design contribute to its increasing prominence, especially where low latency and high performance are paramount.
As both technologies evolve, comparing REST vs gRPC becomes more complex. However, developers often choose the one that aligns with their specific requirements, ensuring a balance between industry-standard practices and emerging solutions.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.