Agentic AI systems rely on fast and reliable communication channels to more natively coordinate and execute tasks among different agents, apps, and services. Efficient communication with external tools is a core tenet of any AI technology, which is what led to the now standard Model Context Protocol (MCP).
Now that agentic AI is becoming a part of real products and business workflows, MCP is drawing global interest, especially across the tech industry.
With any new technology, experimentation on both the malignant and benign side is abundant. New ways for applications to interact with AI agents are exciting to uncover, even if organizations are still in the infancy stages of their journey.
Security controls and frameworks for this new agentic protocol are still immature. As a result, rushing to adopt MCP without careful planning puts security at risk.
Old threats get a new boost
MCP was created with functionality in mind, not security. Since it is constantly under development, it continuously provides a new potential attack surface. The security community is diligently researching this new threatscape and will continue to do so as it evolves further.
Surprisingly (or not really), as companies take baby steps toward real-world agentic systems with its full-blown potential, known and effective web vulnerabilities continue to plague developers. Threats like Structured Query Language injection (SQLi), OS command execution, and server-side request forgery (SSRF) remain material risks — and MCP-based applications give them a new entry point.
Review of the most recent MCP CVEs
According to an Equixly security assessment of the most popular MCP server implementations performed over one month:
43% of them contained command injection vulnerabilities
22% allowed directory traversal or arbitrary file read
30% were vulnerable to SSRF
5% had other security concerns
Recent CVE examples related to classic web vulnerabilities in MCP servers include:
Remote code execution in Anthropic’s MCP Inspector (CVE-2025-49596)
SSRF in Markdownify MCP Server (CVE‑2025‑5276)
Remote code execution in Anthropic’s MCP Inspector (CVE-2025-49596)
MCP Inspector is a developer utility that runs and previews MCP tool workflows. A crafted prompt or tool definition can make the MCP Inspector invoke those tools with attacker-controlled inputs; in vulnerable versions this can lead to arbitrary code execution, local file access, and full compromise of the developer environment.
SSRF in Markdownify MCP Server (CVE‑2025‑5276)
Markdownify is a tool that transforms PDFs, images, web pages, and YouTube videos into Markdown text. An attacker could craft a prompt that, when processed by the MCP host, invokes the webpage-to-markdown, bing-search-to-markdown, and youtube-to-markdown tools to send requests and read responses from attacker-controlled URLs, potentially leaking sensitive information.
Akamai’s native MCP support
MCP provides a direct transport layer for data to flow among apps, partners, and systems, relying on either HTTP/1.1 or HTTP/2.0. Instead of waiting for each request to finish, information can be streamed and updated continuously, thanks to protocols like server-sent events (SSE), which is part of HTTP/1.1, and the more recommended streamable HTTP/2.0. These persistent, high-speed channels drive better efficiency.
As one of the largest reliable and secure medium for HTTP applications worldwide, Akamai natively supports MCP transports, providing out-of-the-box experience and security for any MCP applications deployed through Akamai.
For improved MCP experience over the older SSE transport, response buffering may need adjustment. Practitioners should disable response buffering in the Property Manager configuration (Figure 1).
<network:http.buffer-response-v2>off</network:http.buffer-response-v2>This ensures that SSE data is streamed directly to the client without buffering, preventing idle timeouts and allowing the connection to remain open as intended.
How App & API Protector mitigates vulnerabilities over MCP
Akamai App & API Protector, with its Adaptive Security Engine, can help customers seamlessly mitigate web vulnerabilities over MCP.
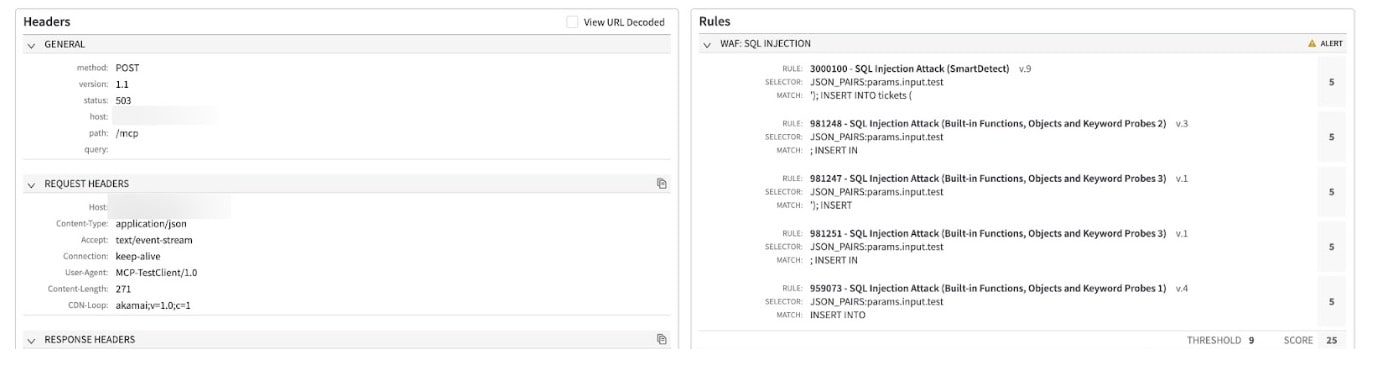
Figure 2 shows how the Adaptive Security Engine mitigated an attack that was discovered in the SQLite MCP server. It also shows how the SQL injection attack group detected the attack initially.
Conclusion
The Model Context Protocol is becoming a critical enabler for AI-driven workflows. While it introduces new unique attack surfaces, the classic web vulnerabilities of hijacking and prompt injection remain a threat and should not be overlooked.
As organizations embrace AI, Akamai remains committed to innovation by helping customers remain safe in the AI era with security that is adaptive, intelligent, and built for what’s next.
Tags