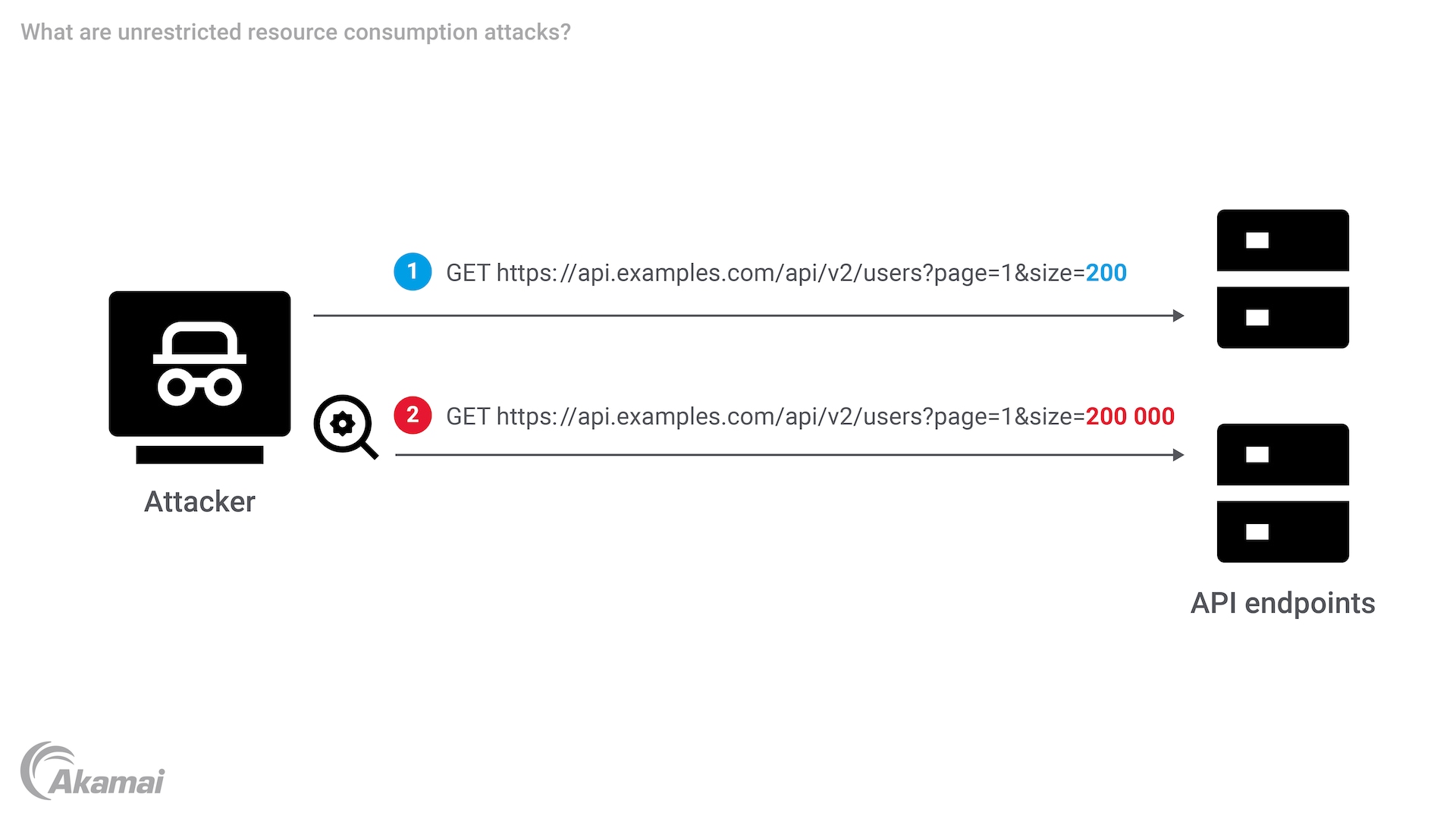
Unrestricted resource consumption refers to the excessive use of API resources by a user or application, leading to increased costs, service disruptions, and potential cybersecurity vulnerabilities. This can occur when an attacker or even an unwitting user overwhelms the API endpoint with requests, causing resource depletion. This issue is especially critical in the context of application security.
What Is Unrestricted Resource Consumption?
Unrestricted resource consumption attacks pose a significant threat to APIs, leading to increased costs, service disruptions, and potential security vulnerabilities. By implementing access control, setting resource limits, rate limiting, securing third-party API integrations, monitoring traffic, and considering spending restrictions, API providers can effectively protect their APIs from these attacks.
Unrestricted resource consumption attacks are a key vulnerability to consider when addressing API security risks, ranked fourth in the OWASP API Security Top 10. In this article, we dive into the details of unrestricted resource consumption attacks on APIs and present effective strategies to safeguard against them.
Understanding unrestricted resource consumption attacks
Unrestricted resource consumption attacks occur when an API user abuses the API by consuming excessive server resources, leading to increased costs and potential service disruptions. This can happen when a user, intentionally or unintentionally, overwhelms the API with requests, causing it to exhaust its limited resources. For example, an attacker may use bots to automatically visit posts or crawl the API excessively, resulting in resource depletion.
The impact of unrestricted resource consumption attacks
Unrestricted resource consumption attacks can have several negative consequences:
- Increased costs: These attacks can lead to increased costs for the API provider, as additional resources may be required to handle the excessive load.
- Service disruptions: These attacks can affect the availability and performance of the API, causing delays and disruptions for legitimate users.
- Unexpected bills: If the API relies on third-party services such as SMS messaging APIs, the attacks can result in unexpected bills and potential service restrictions.
Protecting APIs from unrestricted resource consumption attack
To mitigate the risks associated with unrestricted resource consumption attacks, API providers should implement the following measures:
- Define clear abuse policies: Establish clear policies that outline acceptable API usage and explicitly state the consequences of abuse. These policies should be communicated to API users to ensure they understand the limitations and potential penalties for misuse.
- Implement access control: Implement access control mechanisms to restrict API usage based on user roles and permissions. This helps prevent unauthorized access and allows for better control over resource consumption.
- Set resource limits: Define limits on server resources that API users can consume. By setting appropriate limits, API providers can prevent excessive resource consumption and ensure fair usage among all users.
- Consider rate limiting: Implement rate-limiting mechanisms to restrict the number of requests a user or application can make within a specific time frame. This helps prevent API abuse by limiting the frequency of requests and protecting against brute-force attacks.
- Secure third-party API integrations: When integrating with third-party APIs, ensure that proper security measures are in place. Avoid direct access to sensitive APIs, such as SMS messaging APIs, as attackers can exploit them to consume resources on your behalf. Instead, implement secure and controlled interfaces to interact with third-party services.
- Monitor and analyze traffic: Implement real-time traffic analysis to detect patterns of API abuse. By monitoring API traffic, unusual or suspicious activities can be identified promptly, allowing for timely intervention and mitigation.
- Consider spending restrictions: If possible, set spending restrictions on third-party APIs to prevent unexpected bills. This ensures that API usage remains within budgeted limits and avoids financial surprises.
The role of authentication in preventing unrestricted resource consumption
Authentication plays a critical role in preventing unrestricted resource consumption attacks. By enforcing strong authentication mechanisms, API providers can ensure that only legitimate users with proper credentials can access the API.
Implementing multi-factor authentication (MFA) adds an additional layer of security, making it harder for attackers to misuse the API. Moreover, authentication helps track user activity, enabling providers to identify and limit resource consumption based on user roles and permissions.
The connection between BOLA and unrestricted resource consumption
Broken Object Level Authorization (BOLA) and unrestricted resource consumption are closely related in the context of API security. While BOLA focuses on unauthorized access to specific data objects, unrestricted resource consumption involves the excessive use of API resources. When BOLA is present in an API, attackers can exploit it to consume resources that they should not have access to, leading to a denial of service. By addressing BOLA vulnerabilities through proper authorization checks and access control mechanisms, API providers can reduce the risk of unrestricted resource consumption attacks and protect their server-side resources.
Monitoring and analyzing traffic
To effectively protect APIs from unrestricted resource consumption attacks, it’s essential to monitor and analyze traffic continuously. Real-time traffic analysis tools can detect unusual patterns, such as a sudden spike in API requests or payloads that indicate a potential attack. By implementing server-side validation and filtering mechanisms, providers can block malicious requests before they consume excessive resources. Additionally, setting up alerts for abnormal activity helps providers respond quickly to potential threats, mitigating the impact of an attack.
Frequently Asked Questions
Rate limiting helps prevent unrestricted resource consumption by restricting the number of API requests a user or application can make within a specific time frame. This ensures that no single user can consume an excessive amount of resources, protecting the API from abuse and ensuring fair usage. Properly implementing rate limiting at the API endpoint is a vital aspect of cybersecurity.
Monitoring traffic is crucial because it allows API providers to detect and respond to patterns of abuse. By analyzing traffic in real time at the API endpoint, providers can identify suspicious activities, such as spikes in API requests, and take action to prevent resource exhaustion. This proactive approach is an essential component of application security and overall cybersecurity.
Spending restrictions help protect against unrestricted resource consumption by setting limits on the amount of money that can be spent on third-party API services. This ensures that API usage remains within budgeted limits, preventing unexpected bills and financial strain. Such measures contribute to the broader cybersecurity strategy by limiting potential exploitation of resources.
BOLA can contribute to unrestricted resource consumption attacks by allowing unauthorized users to access and consume resources they shouldn’t. Addressing Broken Object Level Authorization and Broken Object Property Level Authorization (BOPLA) vulnerabilities is crucial in preventing unauthorized resource consumption and protecting API endpoints. By securing these vulnerabilities, API providers can strengthen their cybersecurity posture and ensure robust application security.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.