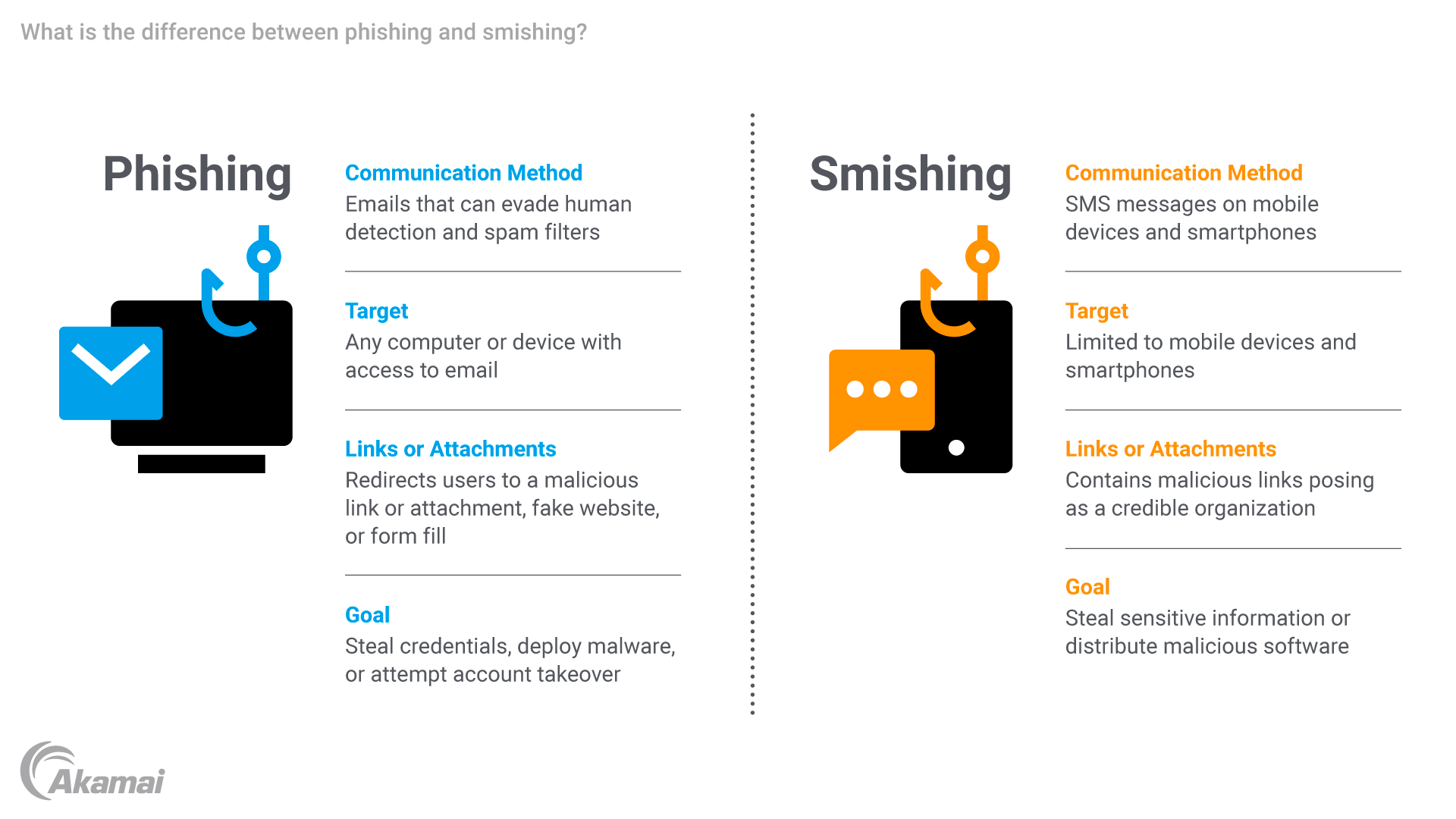
Smishing, a combination of SMS and phishing, refers to phishing attacks conducted via SMS text messages. There are a few key signs that may indicate a smishing attempt. Always beware of text messages from unknown senders or unfamiliar numbers, especially if the message contains several grammatical errors or addresses you by the wrong name. Also, watch out for texts requesting personal information, such as passwords, credit card details, or Social Security numbers.
Some scammers will even use threatening language, posing as an authority figure (e.g., the IRS) or creating a sense of urgency in a smishing attack to convince recipients to provide information before having time to think it over.
Lastly, keep an eye out for suspicious web links. These typically have mismatched, jumbled, or otherwise highly unusual URLs, so check the links before clicking to make sure that everything between www and .com matches reputable websites exactly.