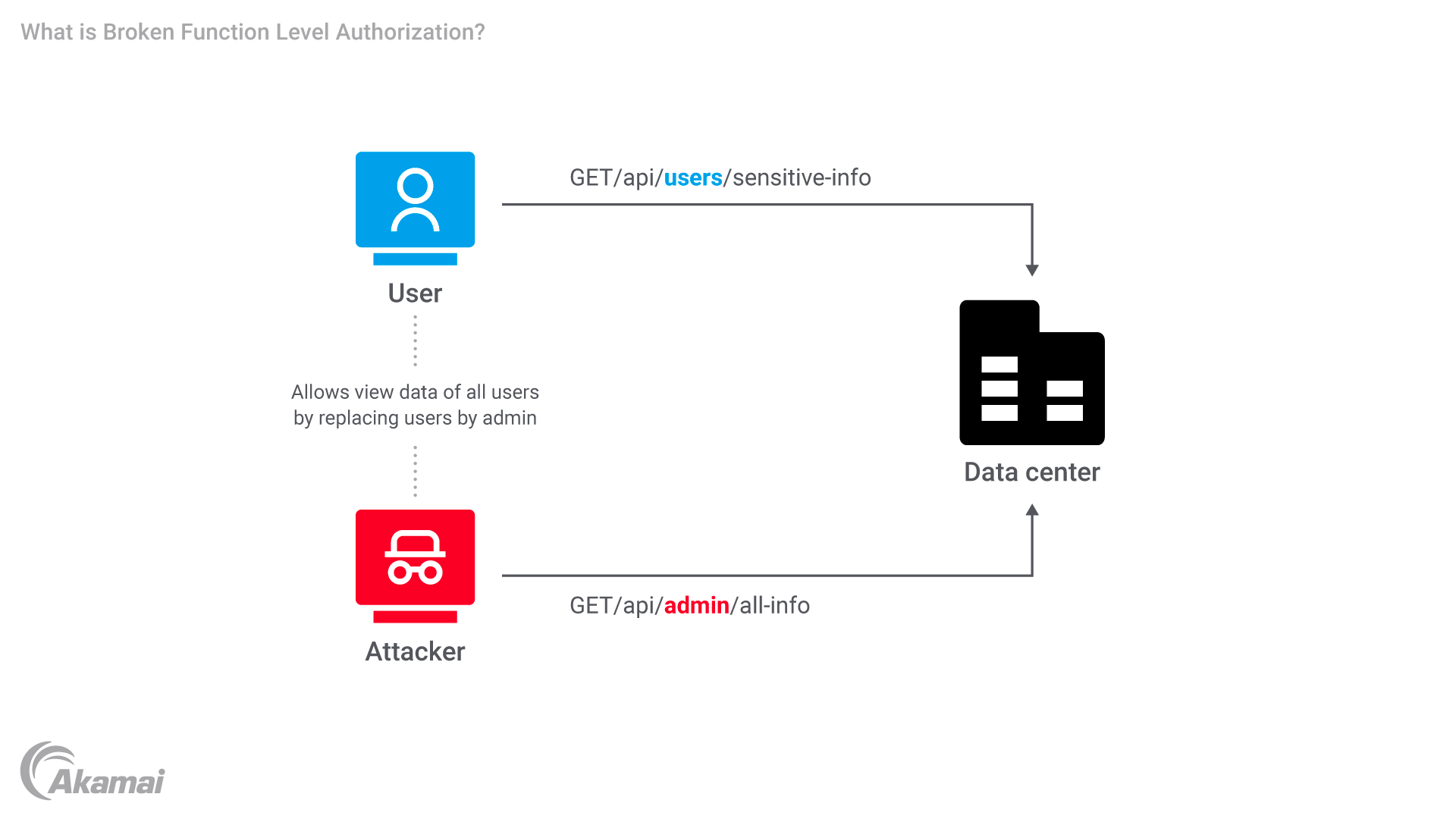
Broken Function Level Authorization is an access control vulnerability in API security that allows attackers to access administrative or authorization mechanisms without the necessary permissions. This occurs when the API fails to enforce proper authorization checks on user roles.
What Is Broken Function Level Authorization?
Broken Function Level Authorization (BFLA) is an important API vulnerability to address. By understanding the risks, implementing proper authorization checks, and following best practices, developers can build secure and resilient APIs. Additionally, leveraging a runtime protection platform like Akamai API Security can provide real-time traffic analysis to detect and block API attacks at critical API endpoints.
In this article, we’ll dive into the concept of Broken Function Level Authorization, which is a type of access control vulnerability in APIs. We will explore its implications, potential risks, and best practices to mitigate this security issue, which is the fifth item in the OWASP API Security Top 10.
Broken Function Level Authorization is a type of access control vulnerability that allows an attacker to perform administrative actions or access privileged API functions without the necessary permissions. It occurs when an API fails to properly enforce authorization checks, enabling unauthorized users to exploit the system. This vulnerability can often be exacerbated by security misconfigurations and improper handling of HTTP methods at the API gateway.
Understanding the access control hierarchy
Access control hierarchies define the permissions and privileges granted to different user roles within an application. In the case of Broken Function Level Authorization, the vulnerability lies in the improper enforcement of these permissions. This can manifest in two ways:
- Vertical privilege escalation: Vertical privilege escalation occurs when a regular user gains access to administrative functionalities or performs actions reserved for higher-level roles. For example, a regular user might be able to delete or modify sensitive data or initiate an account takeover that should only be accessible to administrators.
- Horizontal privilege escalation: Horizontal privilege escalation involves a user gaining unauthorized access to functionalities or data belonging to other organizations or tenants within a multi-tenancy application. This breach of isolation can lead to unauthorized actions and potential data breaches.
Implications and risks
The consequences of Broken Function Level Authorization can be severe. It can lead to unauthorized access, data manipulation, exposure of sensitive information, and a compromise of the entire system’s security. Additionally, it can undermine the trust of users and damage the reputation of the application or organization. This risk is further amplified if there are underlying issues related to broken authentication or security misconfiguration at API endpoints.
The role of authentication in preventing Broken Function Level Authorization
Authentication plays a critical role in mitigating Broken Function Level Authorization vulnerabilities. By ensuring that authentication mechanisms are robust and properly integrated with authorization checks, API providers can significantly reduce the risk of privilege escalation. Implementing strong authentication protocols, such as multi-factor authentication (MFA), helps confirm the identity of users before allowing access to higher-level functions, thereby preventing unauthorized access to administrative functionalities. It’s also crucial to ensure that API functions are protected from common threats such as broken authentication and account takeover attempts.
The connection between BOLA and Broken Function Level Authorization
Broken Object Level Authorization (BOLA) and Broken Function Level Authorization are both important issues in API security. BOLA allows unauthorized access to data, while Broken Function Level Authorization lets attackers gain access to API functions without permission. If an API has BOLA vulnerabilities, it is likely to also have function-level vulnerabilities because both stem from weak authorization checks. To protect server-side operations and prevent denial-of-service (DoS) attacks, it’s essential to address both types of vulnerabilities with strong access control mechanisms. Properly configuring API gateways and HTTP methods is also key to addressing API security risks.
Resolving Broken Function Level Authorization
To mitigate the risks associated with broken function level authorization, consider implementing the following best practices:
- Perform authorization checks: Make sure that every API request includes proper authorization checks to verify the user’s permissions before allowing any action. This involves validating the user’s role and ensuring they have the necessary privileges to perform the requested operation.
- Early access control consideration: Integrate access management early in the development lifecycle. Define and design the access control hierarchy, considering discretionary elements and permission systems. Simplify the permission structure, if possible, to reduce complexity and potential vulnerabilities.
- Avoid middleware authorization: Avoid implementing authorization solely in the middleware layer. Instead, enforce authorization checks at the API level to provide consistent and reliable access control.
- Comprehensive application security program: Establish a comprehensive application security program that supports developers in producing secure code. This program should include regular security training, code reviews, and automated testing to identify and address vulnerabilities, including Broken Function Level Authorization.
Frequently Asked Questions
Authentication ensures that users are who they claim to be. By integrating strong authentication mechanisms with authorization checks, API providers can prevent unauthorized users from accessing privileged functions, thereby mitigating Broken Function Level Authorization vulnerabilities.
BOLA (Broken Object Level Authorization) and Broken Function Level Authorization are related in that both involve improper enforcement of authorization checks. BOLA deals with unauthorized access to data objects, while Broken Function Level Authorization concerns unauthorized access to functions. Addressing both is essential for robust API security.
Server-side validation is crucial because it ensures that all API requests and API calls are properly authenticated and authorized before being processed. This prevents attackers from exploiting function-level vulnerabilities and reduces the risk of denial-of-service (DoS) attacks.
A comprehensive application security program helps prevent Broken Function Level Authorization by providing developers with the tools and training needed to write secure code. Regular security audits, code reviews, and automated testing are essential components of such a program.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.