SCA is an automated process that scans open source software components for vulnerabilities, licensing issues, and compliance with regulatory requirements. It generates a software bill of materials (SBOM) for transparency and security.
With the world of software becoming increasingly complex and interconnected, it’s more important than ever before to scan a codebase for vulnerabilities and maintain an accurate inventory of dependencies before using it or integrating it into one’s own software.
A subset of application security testing, software composition analysis (SCA) refers to an automated process that scans open source code, allowing security analysts to identify precisely which libraries and components have been used in a piece of software. Code is parsed automatically and scanned against a known list of open source vulnerabilities.
Specifically, SCA can be used to inspect:
- Raw source code
- Containers
- Binaries
- Components of an operating system
SCA tools can either be self-standing or integrated into wider-ranging application testing solutions. For instance, one SCA tool may be used to identify what’s running on Linux workstations while another could be used to inspect finished binaries as they move through the DevOps process. They are also commonly used to create a bill of materials (BOM) for software developers. BOMs will list all the components used in a piece of software, allowing the security team to flag any potential vulnerabilities.
SCA tools can also be used to identify the licenses associated with any open source components integrated into a piece of delivered software. Open source doesn’t necessarily mean free, and by scanning codebases for licenses, developers can avoid costly fines and reputational damage.
How does software composition analysis work?
At its core, SCA involves parsing a codebase to identify and evaluate third-party components. This analysis is performed against databases like the National Vulnerability Database (NVD), open source vulnerability repositories, and proprietary threat intelligence sources. Integrating SCA tools into continuous integration pipelines automates the scanning and analysis of open source components, allowing for early detection of vulnerabilities and compliance issues.
Key processes include:
- Dependency mapping: SCA tools identify all dependencies in the software, including direct and transitive dependencies (libraries used by other libraries). This creates a complete inventory of the software's third-party components. Dependency graphs are used to identify both direct and indirect vulnerabilities, prioritizing those that affect the execution path.
- Vulnerability scanning: Each component is analyzed against known vulnerabilities, such as those listed in Common Vulnerabilities and Exposures (CVEs). This helps developers address security risks early in the software development lifecycle (SDLC).
- License compliance checks: SCA tools scan for open source licenses and identify potential conflicts with organizational policies, such as the use of restrictive licenses (e.g., GPL or AGPL).
- Software bill of materials (SBOM) creation: A software bill of materials (SBOM) is generated, providing a detailed list of all components, versions, and their associated metadata. This is critical for transparency, regulatory compliance, and incident response.
- Remediation guidance: When vulnerabilities or license issues are identified, SCA tools provide actionable insights, such as upgrading to safer library versions or replacing problematic components.
Why is SCA essential?
SCA has become indispensable for organizations leveraging open source software. Its importance stems from several critical factors:
- Increased use of open source: More than 90% of modern applications incorporate open source components. While cost-effective, these components often introduce vulnerabilities that require proactive management.
- Software supply chain security: High-profile supply chain attacks (e.g., SolarWinds, Log4Shell) have underscored the importance of securing third-party dependencies. SCA tools help organizations identify outdated dependencies and mitigate security risks across their software supply chain.
- Regulatory compliance: Regulations like GDPR, PCI DSS, and the U.S. cybersecurity Executive Order mandate secure software practices, including maintaining an SBOM. SCA ensures adherence to these requirements.
- Improved code quality and security: By detecting vulnerable or outdated components, SCA enhances the overall security posture and code quality of applications.
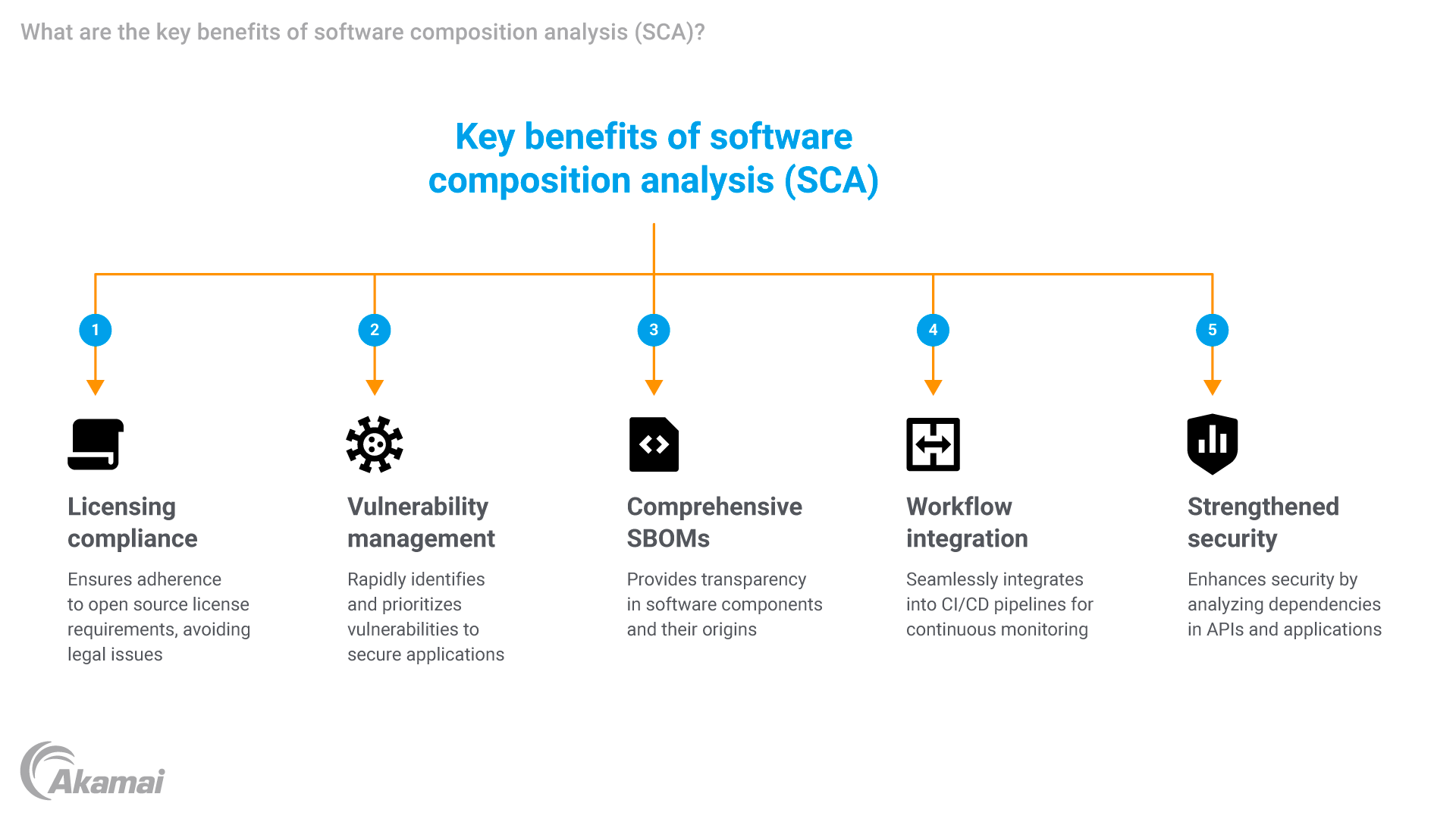
Key benefits of SCA
1. Licensing compliance
SCA tools ensure organizations respect open source license requirements, avoiding potential legal penalties or reputational damage. This is especially important for restrictive licenses like GPL, which require disclosure of derivative works.
2. Vulnerability management
SCA tools rapidly identify vulnerabilities in open source components, enabling developers to prioritize remediation efforts. This reduces the attack surface and ensures secure application development.
3. Comprehensive SBOMs
An SBOM lists all software components, their versions, and their origins. This transparency simplifies incident response, aids compliance, and fosters trust with customers and stakeholders.
4. Enhanced workflow integration
Modern SCA tools integrate seamlessly into CI/CD pipelines, enabling continuous monitoring and remediation without disrupting development workflows.
5. Strengthened API and application security
By analyzing dependencies used in APIs and applications, SCA tools help secure endpoints, reduce attack vectors, and enhance overall application security.
Advanced use cases for SCA
1. Securing cloud-native applications
In cloud native environments, applications rely heavily on containerized microservices. SCA tools can scan containers for vulnerable dependencies, ensuring secure deployments across Kubernetes clusters and other orchestration platforms.
2. Incident response and forensics
When a vulnerability like Log4Shell is disclosed, SCA tools can quickly identify which applications and systems are affected, enabling rapid incident response and patching.
3. Risk-based prioritization
SCA tools leverage risk scoring to prioritize vulnerabilities based on severity, exploitability, and business impact. This allows security teams to focus on the most critical issues.
4. Continuous monitoring
SCA extends beyond point-in-time scans, offering continuous monitoring for new vulnerabilities in existing software components.
SCA vs. other application security testing tools
SCA vs. static application security testing (SAST)
- SCA: Focuses on open source components, identifying vulnerabilities and license issues. It also integrates security vulnerability detection to enhance software security.
- SAST: Analyzes proprietary source code for vulnerabilities, ensuring secure coding practices.
SCA vs. dynamic application security testing (DAST)
- SCA: Operates statically, without requiring a running application. It scans open source components for known vulnerabilities, identifying security flaws to proactively address potential weaknesses.
- DAST: Scans live applications for runtime vulnerabilities.
SCA vs. static composition analysis (SCA)
The term “SCA” can also refer to static code analysis. While both involve code analysis, static code analysis focuses on syntax and logic errors, while software composition analysis emphasizes open source dependencies.
Challenges and limitations of SCA
While SCA offers significant benefits, it is not without limitations:
- False positives: Overly broad scans can produce false positives, requiring manual validation.
- Runtime blind spots: SCA cannot detect runtime vulnerabilities or misconfigurations.
- Limited proprietary code analysis: SCA focuses solely on open source components, necessitating complementary tools like SAST for proprietary code.
Frequently Asked Questions
SCA identifies vulnerabilities in open source dependencies, ensuring they are remediated before they can be exploited. It also provides visibility into third-party components, reducing the attack surface.
Yes, modern SCA tools integrate seamlessly with CI/CD workflows, enabling continuous monitoring and remediation during development and deployment.
SCA detects vulnerabilities in open source components, such as those listed in Common Vulnerabilities and Exposures (CVEs), including SQL injection, buffer overflows, and cross-site scripting (XSS).
While not always mandated, SCA is essential for meeting regulatory requirements like SBOMs in the U.S. Cybersecurity Executive Order, GDPR, and PCI DSS.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.