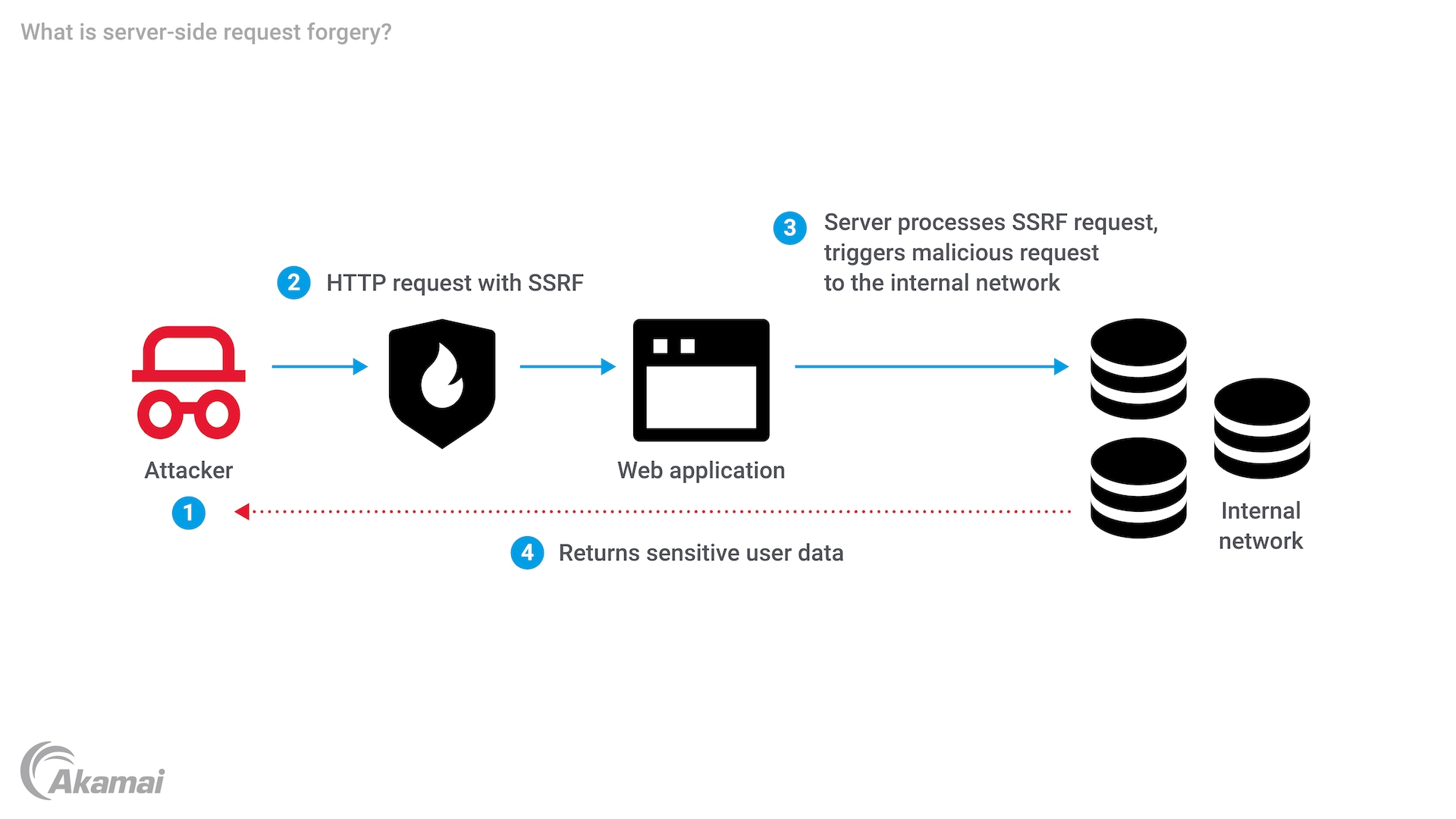
Understanding server-side request forgery (SSRF) is essential for web security as it poses a substantial risk to the confidentiality and integrity of web applications and the systems they rely on.
By understanding SSRF and its potential impact on web application security, developers and security professionals can implement appropriate mitigation measures, such as enforcing strict access controls and restricting the destinations of server-side requests. Additionally, testing for security misconfiguration and vulnerability assessments should include checks for SSRF vulnerabilities to identify and remediate any weaknesses before attackers can exploit them.