The primary purpose of a firewall is to enforce security policies by examining data packets and determining whether they should be allowed to pass through the network. By filtering out malicious or unwanted traffic, firewalls help to safeguard sensitive data and maintain the integrity of network connections.
What Is a Firewall?
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between trusted internal networks and untrusted external networks, such as the internet, to prevent unauthorized access and malicious traffic. Firewalls are essential components in any cybersecurity strategy, providing a crucial layer of protection against potential threats and vulnerabilities.
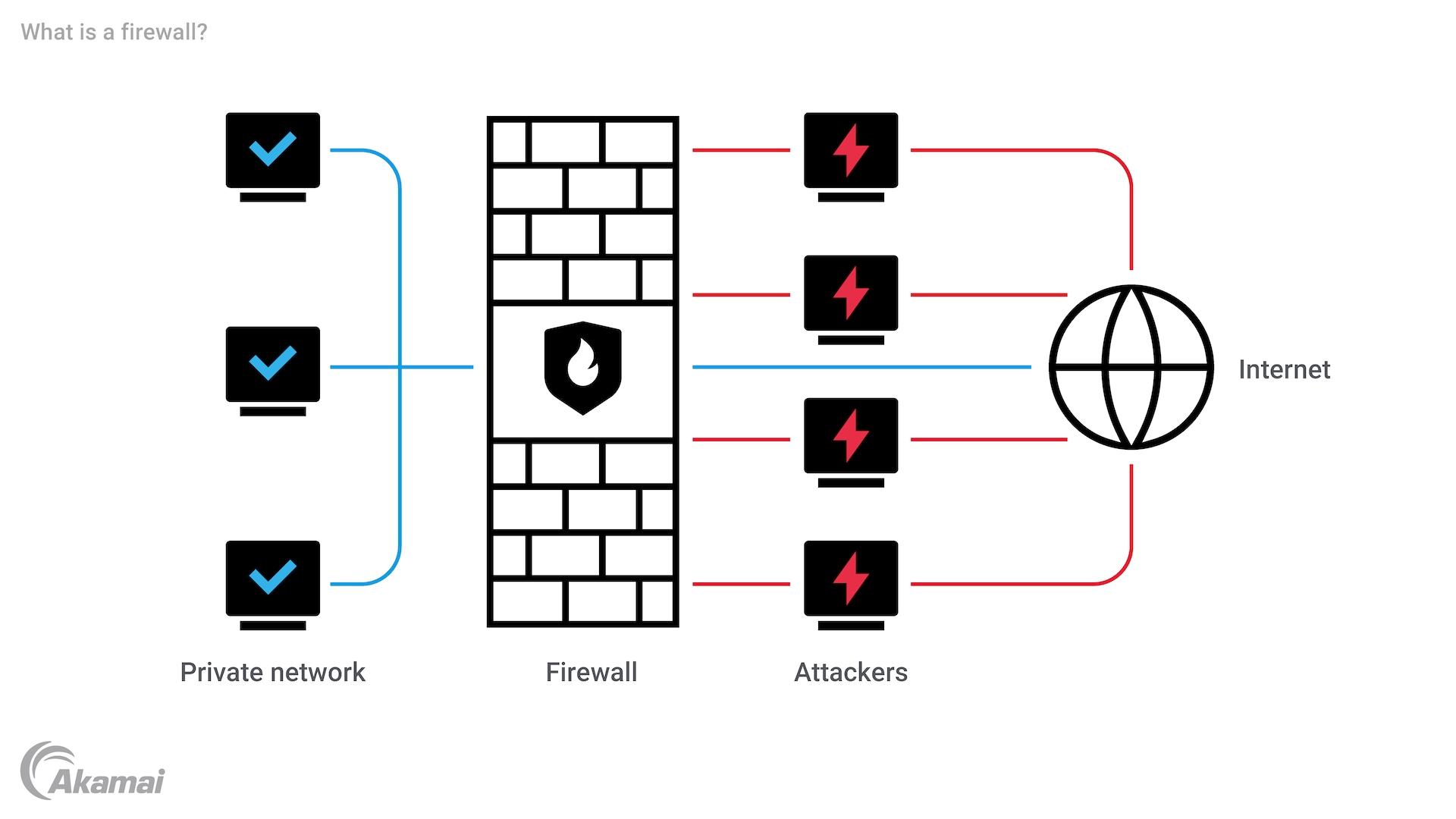
The primary purpose of a firewall is to enforce security policies by examining data packets and determining whether they should be allowed to pass through the network. By filtering out malicious or unwanted traffic, firewalls help to safeguard sensitive data and maintain the integrity of network connections. This real-time monitoring and filtering process is fundamental to maintaining network security and preventing breaches.
Firewalls can be hardware-based, software-based, or a combination of both. Hardware firewalls are typically integrated into routers and other network devices, while software firewalls are installed on individual endpoints. Both types play a critical role in protecting against unauthorized access and ensuring that network traffic adheres to predefined security policies.
Exploring types of firewalls
There are several types of firewalls, each with its own unique approach to managing network traffic and enforcing security policies. Packet-filtering firewalls, stateful inspection firewalls, proxy firewalls, and next-generation firewalls (NGFWs) each offer different levels of protection and functionality. Understanding the differences between these types is essential for selecting the right firewall for your network environment.
Packet-filtering firewalls operate at the network layer of the Open Systems Interconnection (OSI) model and filter traffic based on IP addresses, port numbers, and protocol types. They are simple and efficient but may not provide the same level of security as more advanced firewalls.
Stateful inspection firewalls, on the other hand, maintain context about active connections and use this information to make more informed decisions about allowing or blocking traffic. This makes them more effective at detecting and blocking sophisticated attacks.
Proxy firewalls, also known as application-level gateways, operate at the application layer of the OSI model. They act as intermediaries between clients and servers, inspecting and filtering traffic at a deeper level. Proxy firewalls can provide more granular control over network traffic and are particularly useful for protecting against application-layer attacks and malware. However, they can introduce additional latency and may require more resources to manage.
Next-generation firewalls (NGFWs) represent a significant advancement in firewall technology. These firewalls combine traditional firewall capabilities with advanced threat protection features, such as deep packet inspection (DPI), intrusion prevention systems (IPS), and malware defense. NGFWs are designed to address the evolving landscape of cyberthreats by providing more comprehensive and dynamic security solutions. They are particularly effective in cloud environments and data centers, where the need for advanced threat protection is paramount.
How firewalls work: a technical overview
Firewalls work by monitoring and controlling network traffic in real time. They use a combination of IP addresses, TCP headers, and other network protocols to analyze and filter data packets. By examining the source and destination IP addresses, port numbers, and other relevant information, firewalls can determine whether a packet should be allowed to pass through or be blocked.
One of the key functions of a firewall is to manage vulnerabilities and prevent unauthorized access. By enforcing strict security policies and filtering out malicious traffic, firewalls help to protect against a wide range of threats, including hackers, malware, and other forms of cyberattacks. This is particularly important in cloud environments, where the attack surface is often larger and more complex.
Firewall work is not limited to just blocking traffic; it also involves monitoring network connections and identifying potential threats. This real-time security solution is essential for maintaining the integrity of network traffic and ensuring that sensitive data remains protected. By integrating with other security tools, such as antivirus software and IPS, firewalls can provide a more robust and layered approach to cybersecurity.
Checking and managing your firewall
Regularly checking and managing your firewall is crucial for maintaining network security. To verify the status of your firewall, you can access the settings on your router or endpoint devices. Most modern routers and operating systems provide user-friendly interfaces for configuring firewall settings, allowing you to review and adjust security rules as needed.
For more advanced management, you can use specialized tools and services to optimize firewall security. These tools can help you automate the process of updating security policies, integrating threat intelligence, and monitoring network traffic. By leveraging these resources, you can ensure that your firewall is always up to date and capable of defending against the latest threats.
When deciding whether to turn your firewall on or off, it's important to weigh the potential risks against the benefits. While turning off the firewall may improve network performance in some cases, it significantly increases the risk of unauthorized access and malicious activity. In cloud environments and internal networks, maintaining a robust firewall is essential for protecting sensitive data and ensuring the overall security of your network.
Leveraging firewall technology for enhanced cybersecurity
Firewalls play a critical role in modern security solutions, serving as the first line of defense against unauthorized access and malicious traffic. By effectively managing network traffic and enforcing strict security policies, firewalls help to safeguard sensitive data and maintain the integrity of network connections. Whether you are using a traditional packet-filtering firewall, a stateful inspection firewall, a proxy firewall, or a NGFW, the importance of firewall technology cannot be overstated.
As the threat landscape continues to evolve, the role of firewalls in cybersecurity will only become more significant. Trends in firewall technology, such as firewall as a service (FWaaS) and virtual firewalls, will provide even more flexible and scalable solutions for protecting against advanced threats. By leveraging these advancements, organizations can enhance their cybersecurity posture and better protect their data centers, cloud environments, and internal networks.
In conclusion, firewalls are an indispensable component of any comprehensive cybersecurity strategy. By understanding the different types of firewalls, how they work, and how to manage them effectively, you can ensure that your network remains secure and resilient against a wide range of threats. Whether you are a small business or a large enterprise, investing in robust firewall technology is a critical step in safeguarding your digital assets and maintaining the trust of your customers and partners.
Frequently Asked Questions
The three main types of firewalls are packet-filtering firewalls, stateful inspection firewalls, and proxy firewalls. Each type offers different levels of protection and functionality, with next-generation firewalls (NGFWs) representing a significant advancement by combining traditional firewall capabilities with advanced threat protection features.
Packet-filtering firewalls operate at the network layer of the OSI model and filter traffic based on IP addresses, port numbers, and protocol types. They are simple and efficient but may not provide the same level of security as more advanced firewalls.
Stateful inspection firewalls maintain context about active connections and use this information to make more informed decisions about allowing or blocking traffic. This makes them more effective at detecting and blocking sophisticated attacks compared to packet-filtering firewalls, which only filter traffic based on IP addresses, port numbers, and protocol types.
A proxy firewall, also known as an application-level gateway, operates at the application layer of the OSI model. It acts as an intermediary between clients and servers, inspecting and filtering traffic at a deeper level. This provides more granular control over network traffic and is particularly useful for protecting against application-layer attacks and malware.
Next-generation firewalls (NGFWs) combine traditional firewall capabilities with advanced threat protection features, such as deep packet inspection (DPI), intrusion prevention systems (IPS), and malware defense. NGFWs are designed to address the evolving landscape of cyberthreats by providing more comprehensive and dynamic security solutions, making them particularly effective in cloud environments and data centers.
Firewalls help manage vulnerabilities and prevent unauthorized access by enforcing strict security policies and filtering out malicious traffic. They monitor network traffic in real time, examining the source and destination IP addresses, port numbers, and other relevant information to determine whether a packet should be allowed to pass through or be blocked.
Regularly checking and managing your firewall is crucial for maintaining network security. This involves accessing the settings on your router or endpoint devices to review and adjust security rules as needed. Advanced management tools can help automate the process of updating security policies, integrating threat intelligence, and monitoring network traffic.
Turning off your firewall can significantly increase the risk of unauthorized access and malicious activity. While it may improve network performance in some cases, the potential security risks far outweigh the benefits. In cloud environments and internal networks, maintaining a robust firewall is essential for protecting sensitive data and ensuring the overall security of your network.
Firewalls can be integrated with other security tools, such as antivirus software and intrusion prevention systems (IPS), to provide a more robust and layered approach to cybersecurity. This integration allows for real-time monitoring, threat detection, and rapid response to potential security incidents, enhancing the overall security posture of the network.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.


